Description
Plattform: Hack the Box
Link: https://app.hackthebox.com/challenges/525
Difficulty: easy 🟢
Introduction
After gaining access to the enemy infrastructure, we have collected critical network traffic data from their Modbus network. Our primary objective is to quickly identify the specific registers containing highly sensitive information and extract this data.
Scope
- Identify important traffic in the PCAP file
- Extract information from the PLC
Traffic analysis
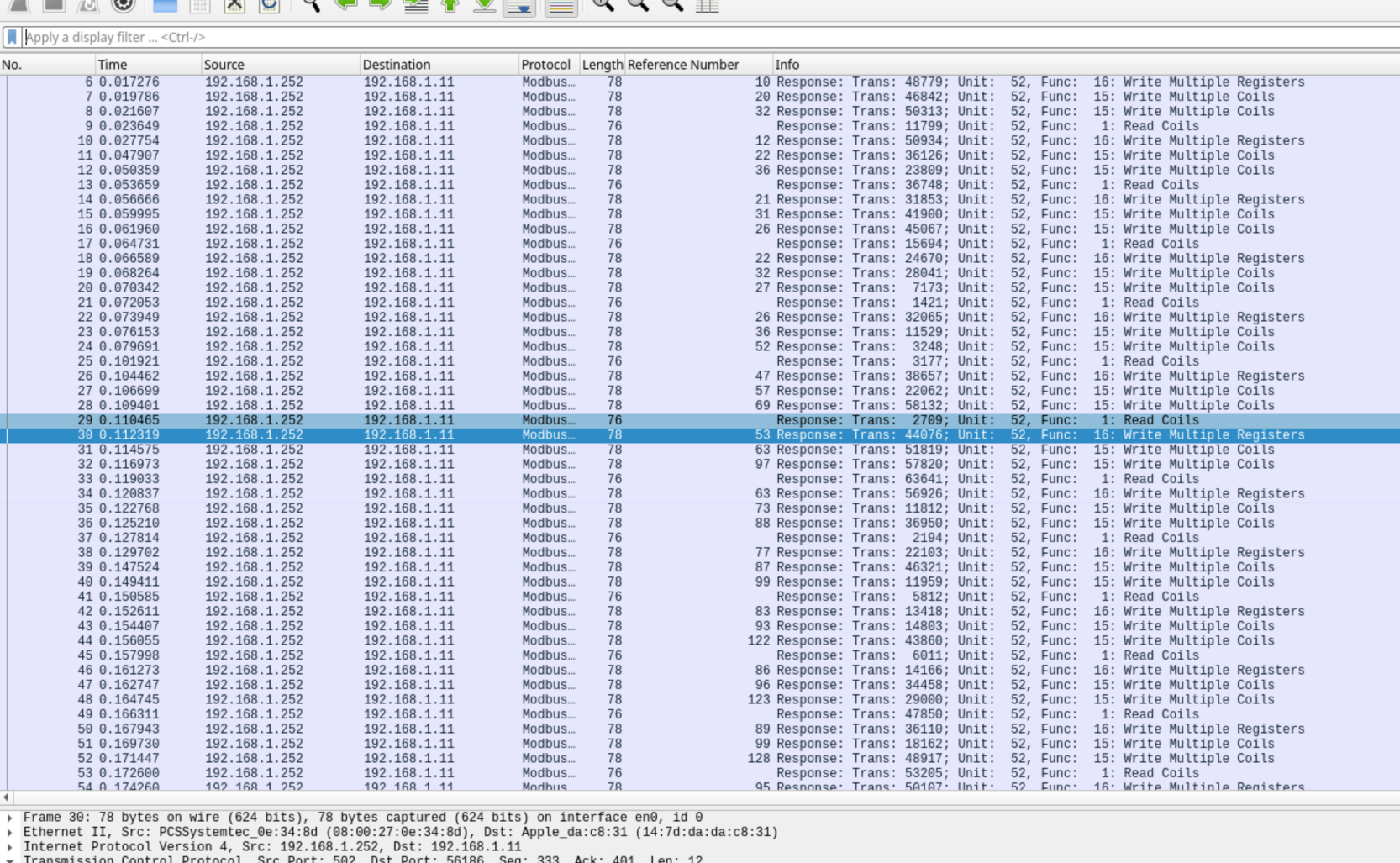
In this case, the „Write Multiple Coils“ traffic is of interest, specifically Function Code 16 (FC-16).
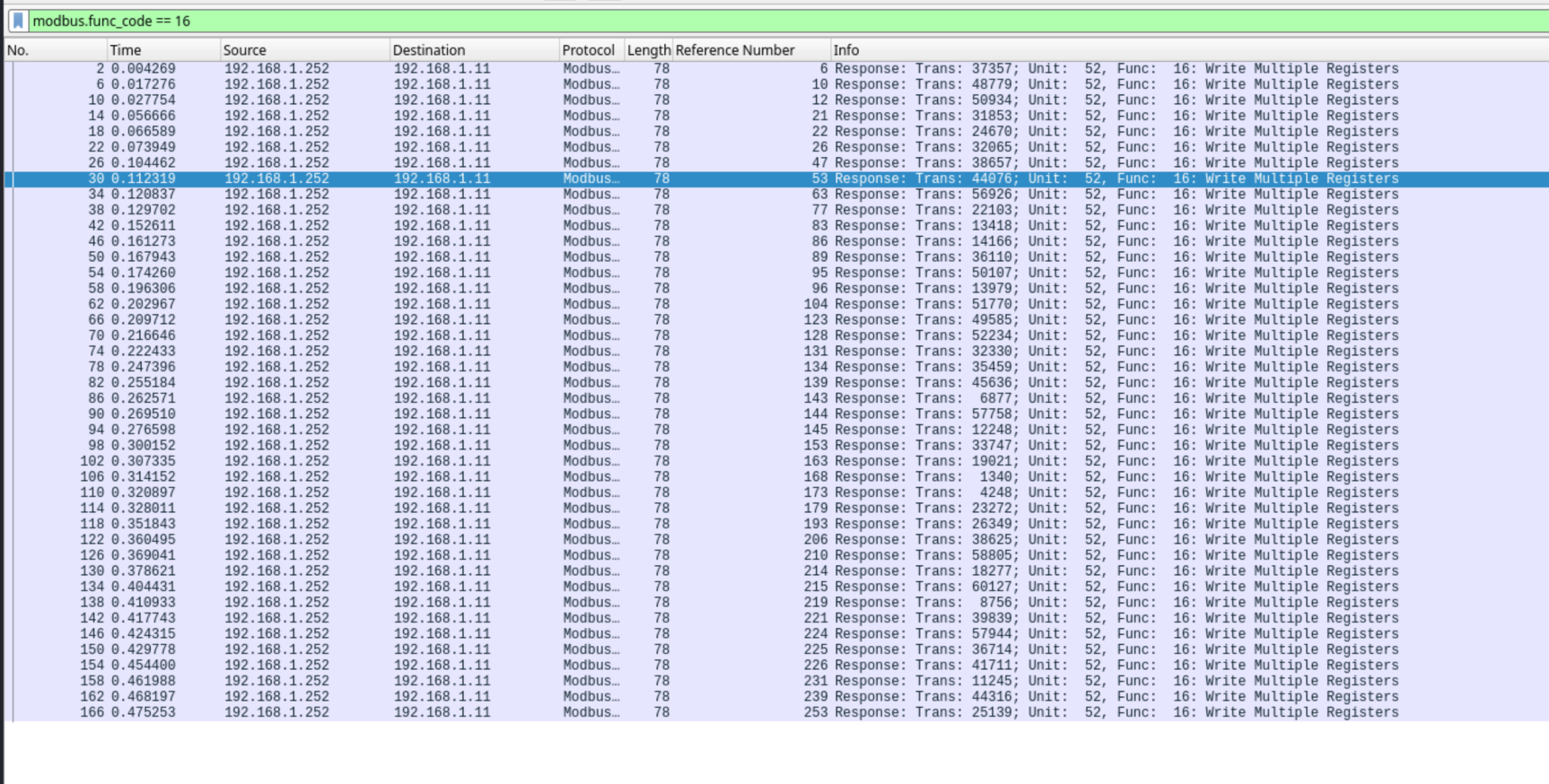
You could manually extract the data, or alternatively, use Tshark to output it directly.
shark -r network_logs.pcapng -Y "modbus.func_code == 16" -T fields -e modbus.reference_numReading Registers from the PLC
Now, the values of individual registers need to be read. This can be done using the script from the download files or by writing a custom script.
I preferred to build my own:
from pyModbusTCP.client import ModbusClient
HOST = "94.237.60.64"
PORT = 51447
UNIT_ID = 52 # Unit-ID
registers = [
6, 10, 12, 21, 22, 26, 47, 53, 63, 77, 83, 86, 89, 95, 96, 104, 123, 128, 131, 134,
139, 143, 144, 145, 153, 163, 168, 173, 179, 193, 206, 210, 214, 215, 219, 221, 224,
225, 226, 231, 239, 253
]
client = ModbusClient(host=HOST, port=PORT, unit_id=UNIT_ID, auto_open=True)
if not client.open():
print("Error: Connection failed!")
exit()
result_text = ""
for reg in registers:
val = client.read_holding_registers(reg, 1)
if val is None:
print(f"Error: Unable to read Reg {reg}")
continue
raw_text = "".join(chr(v >> 8) + chr(v & 0xFF) for v in val)
#Filter charackters
cleaned_text = "".join(c for c in raw_text if 32 <= ord(c) <= 126)
result_text += cleaned_text
client.close()
print(result_text)If everything was done correctly, the flag will be displayed.
