Introduction
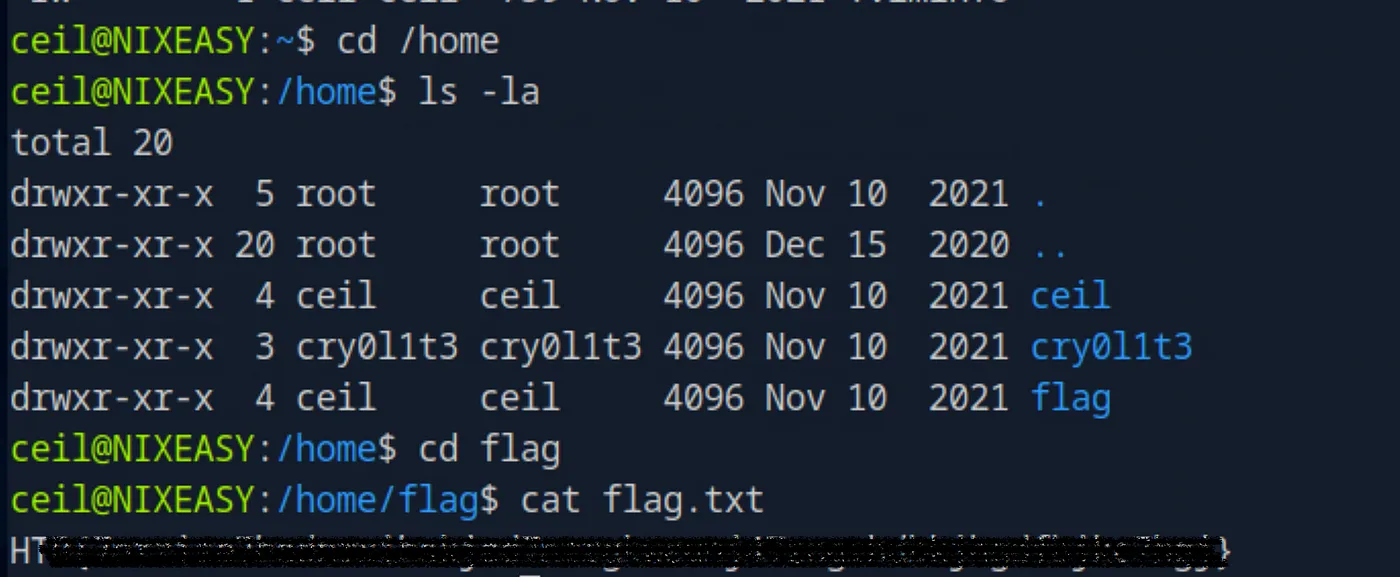
Inlanefreight Ltd has commissioned a penetration test on their internal network to assess security. The focus is on an internal DNS server, with the goal of gathering information without using aggressive attacks or exploits. Credentials (“ceil:qwer1234”) have been found, and there are indications of SSH keys. A file named `flag.txt` is located on the server, and its contents are to be submitted as proof of progress.
Enumeration
NMAP
First of all we want to get a clear picture of the target system, to which serivces are running and which ports are open.
nmap -A -T5 -sC -sV IPPORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (ftp.int.inlanefreight.htb) [10.129.227.28]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3f:4c:8f:10:f1:ae:be:cd:31:24:7c:a1:4e:ab:84:6d (RSA)
| 256 7b:30:37:67:50:b9:ad:91:c0:8f:f7:02:78:3b:7c:02 (ECDSA)
|_ 256 88:9e:0e:07:fe:ca:d0:5c:60:ab:cf:10:99:cd:6c:a7 (ED25519)
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
2121/tcp open ccproxy-ftp?
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (Ceil's FTP) [10.129.227.28]
| Invalid command: try being more creative
|_ Invalid command: try being more creativeOn port 2121, there is an FTP server named “Ceil’s FTP” — the credentials mentioned in the introduction might work here.
FTP-Server
ftp -p ceil@IP 2121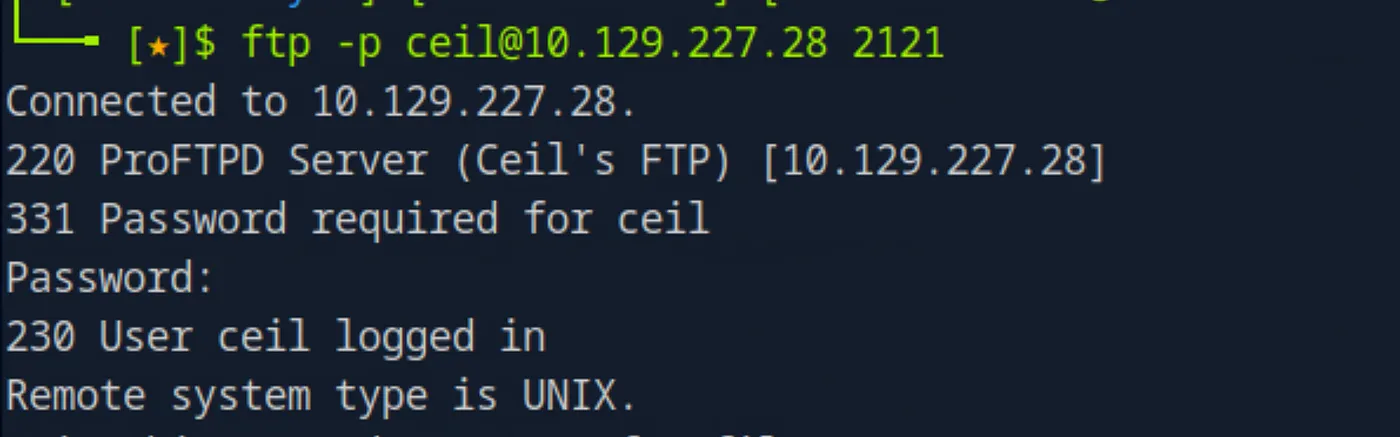
And it worked; we can log into the FTP server with the user credentials. It’s important to specify the correct port. Although we can also log into the other FTP server running on port 21, we won’t find anything useful there.
On the FTP server, we find several directories, including `.ssh`, which contains an SSH key. Reviewing the `.bash_history` file suggests that Ceil created a new key here and stored it in this directory.
We can download the ssh-key with the following command:
get_id_rsaWe can then use this SSH key to connect to the server via SSH. However, we first need to set the correct permissions for the key.
. ssh/ directory: 700 ( drwx------ )
public key ( . pub file): 644 ( -rw-r--r-- )
private key ( id_rsa ): 600 ( -rw------- )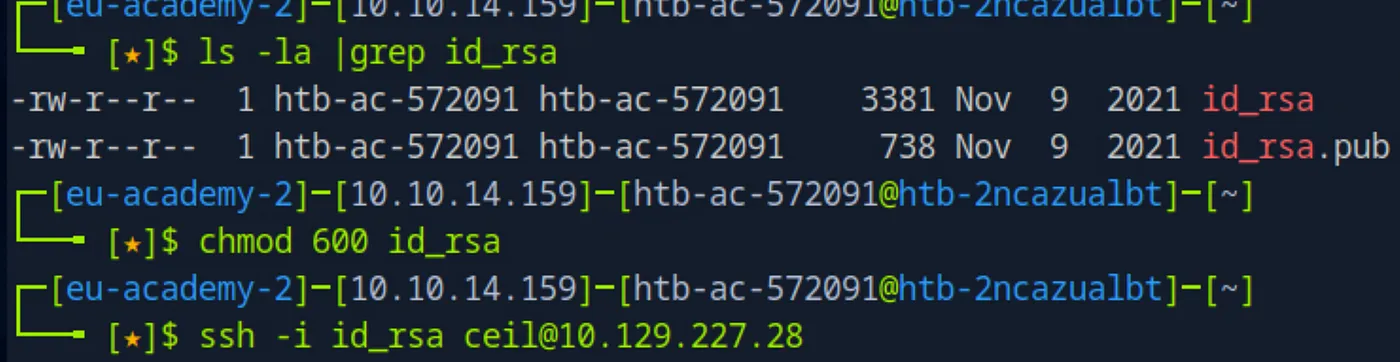
chmod 600 id_rsaSSH Connection
We can use the key to connect to the system with the following command
ssh -i id_rsa ceil@ip In the `/home/` directory, there is a folder named “flag,” where we find the required flag.