Introduction
This is a second server that is accessible to everyone in the internal network. The client was informed that such servers are often targeted by attackers and has included this server in the scope. The goal is to gather information about the server and exploit any potential vulnerabilities. Additionally, a user named HTB has been created, and its credentials need to be obtained as proof.
Enumeration
NMAP
PORT STATE SERVICE VERSION
111/tcp open rpcbind?
| rpcinfo:
| program version port/proto service
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 4 2049/tcp nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open nlockmgr 1-4 (RPC #100021)
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-11-07T10:55:25+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=WINMEDIUM
| Not valid before: 2024-11-06T10:49:02
|_Not valid after: 2025-05-08T10:49:02
| rdp-ntlm-info:
| Target_Name: WINMEDIUM
| NetBIOS_Domain_Name: WINMEDIUM
| NetBIOS_Computer_Name: WINMEDIUM
| DNS_Domain_Name: WINMEDIUM
| DNS_Computer_Name: WINMEDIUM
| Product_Version: 10.0.17763
|_ System_Time: 2024-11-07T10:55:17+00:00We find some NFS-Shares, we can inspect them deeper with the right nmap-script.
nmap --script=nfs* 10.129.79.55 -sV -p111,2049While checking the output of the script, one share “TechSupport” catches our interest.
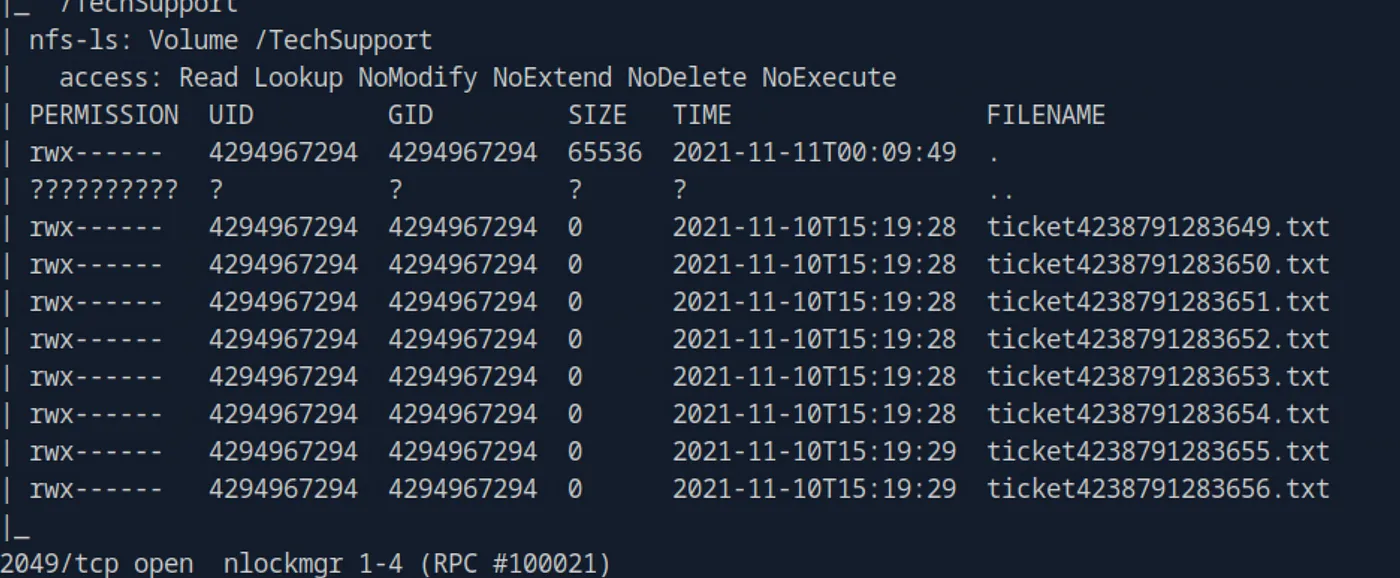
NFS-Share
We can try to mount the share…
1. Create mountpoint
mkdir techsupport2. Mount the share to the directory
sudo mount -t nfs 10.129.79.55:/TechSupport ./techsupport -o nolockTo access the share we need to switch to the root-user
sudo suIf we take a closer look at the contents of the folder, it becomes apparent that all the files seem to be empty, except for one.
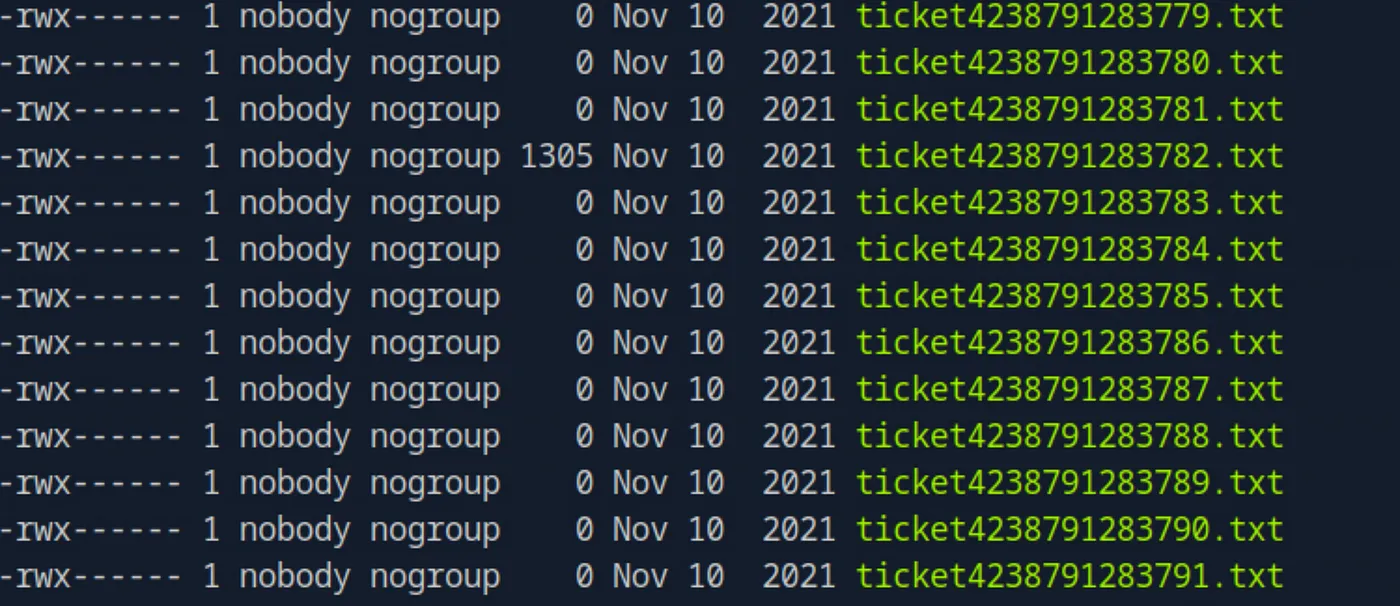
We can view the ticket using `cat *` and notice that it appears to contain correspondence with support regarding the server configuration. The ticket history also reveals useful credentials.
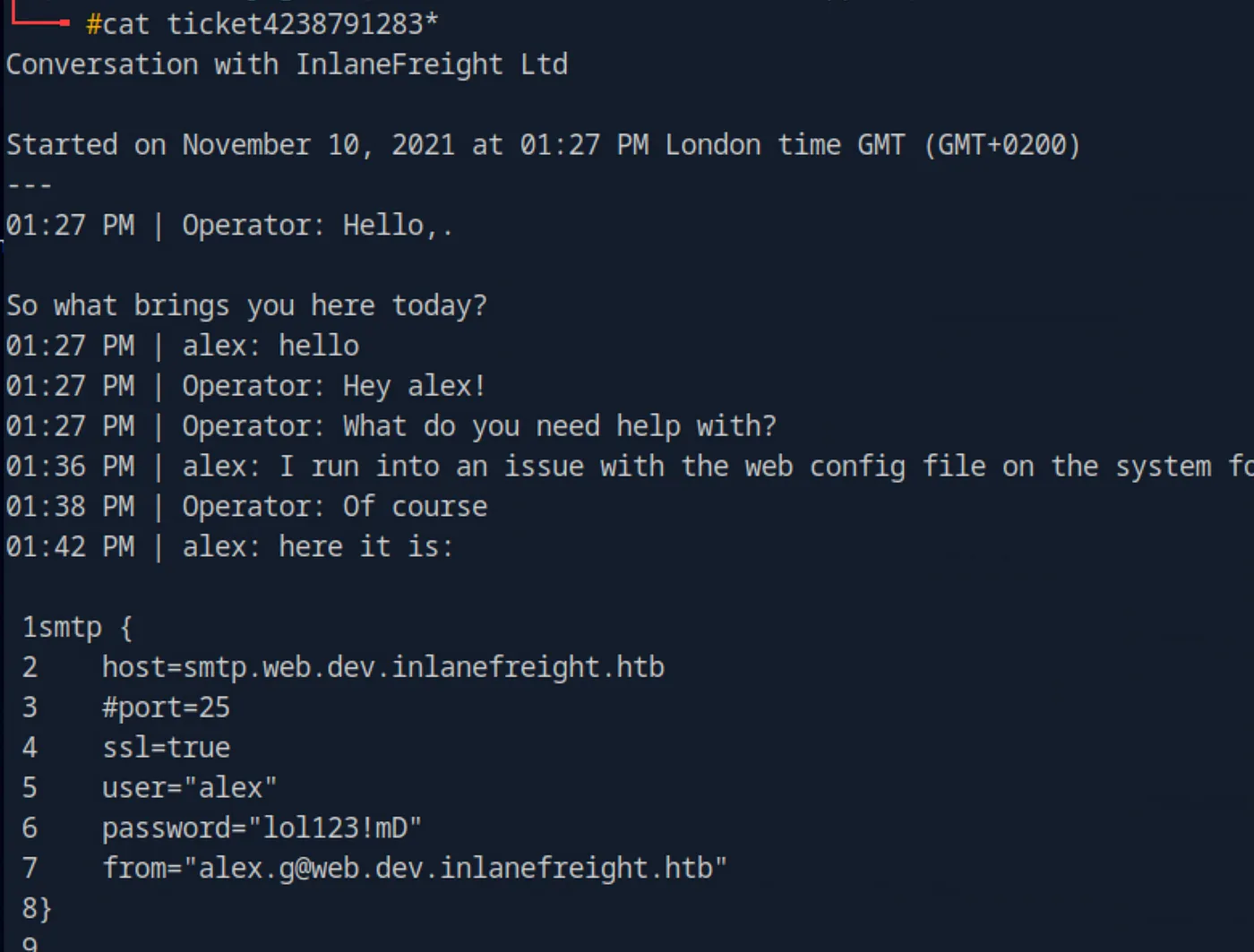
user="alex"
password="lol123!mD"
from="[email protected]"Initial Foothold
Remote Desktop
We recall from the NMAP scan that RDP was active on the server. Using the credentials, we attempt to connect to the system via RDP. We can use Remmina for this purpose.
And indeed, the attempt is successful, and we can log in as the user “alex” on the system. On the desktop, there is a shortcut for MSSQLS MS, which already has a user saved for the login: “sa”, but no password. We try using Alex’s password.
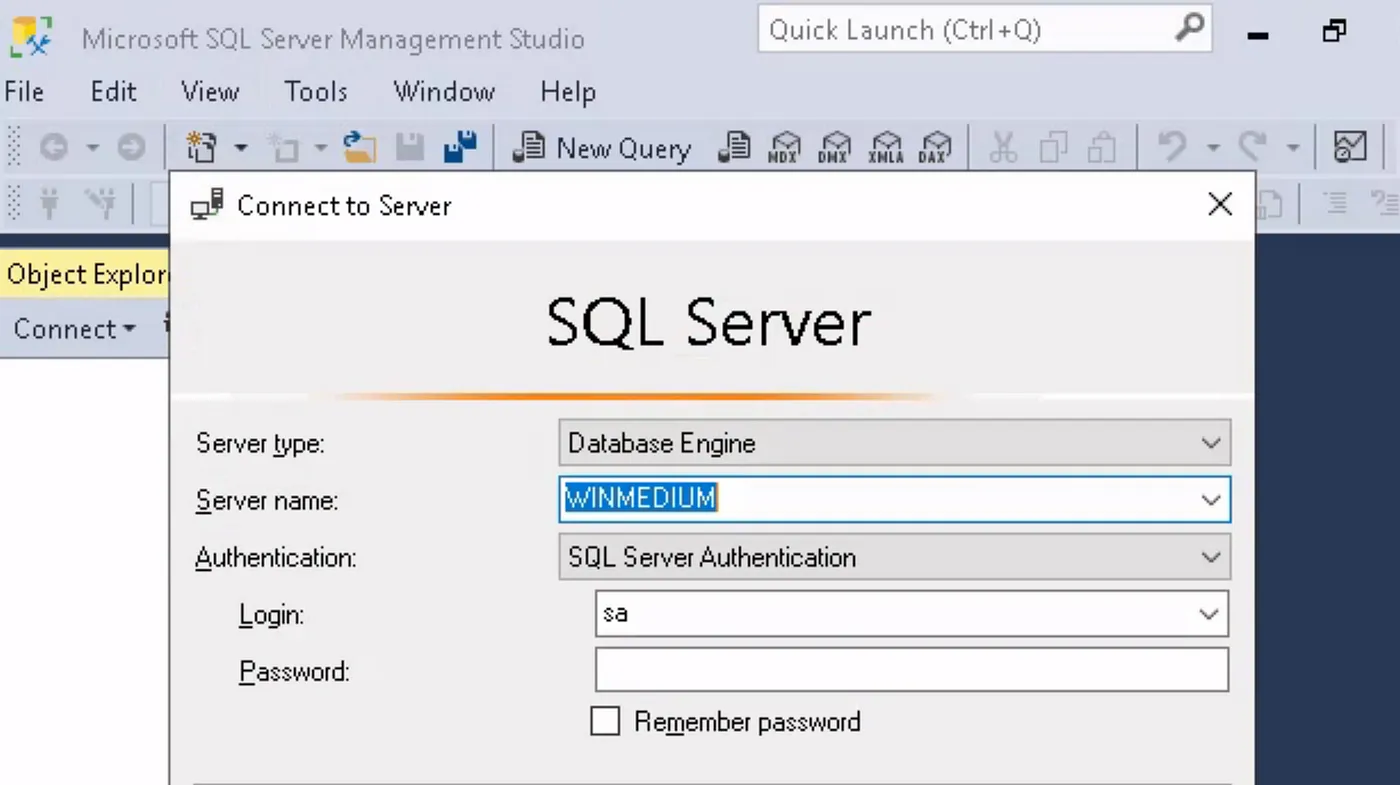
It seems we need to find the credentials first. When we look around in Alex’s user folder, the “Devshare” folder stands out.
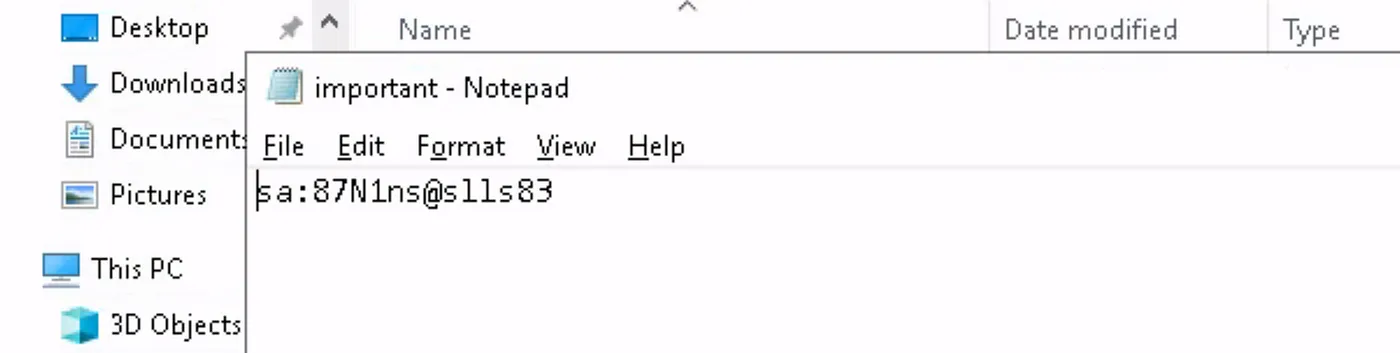
User: sa
PW: 87N1ns@slls83However, when attempting to connect, we encounter an error. Let’s try running MSSQLS MS as an administrator instead. We apparently just found the password for this account.
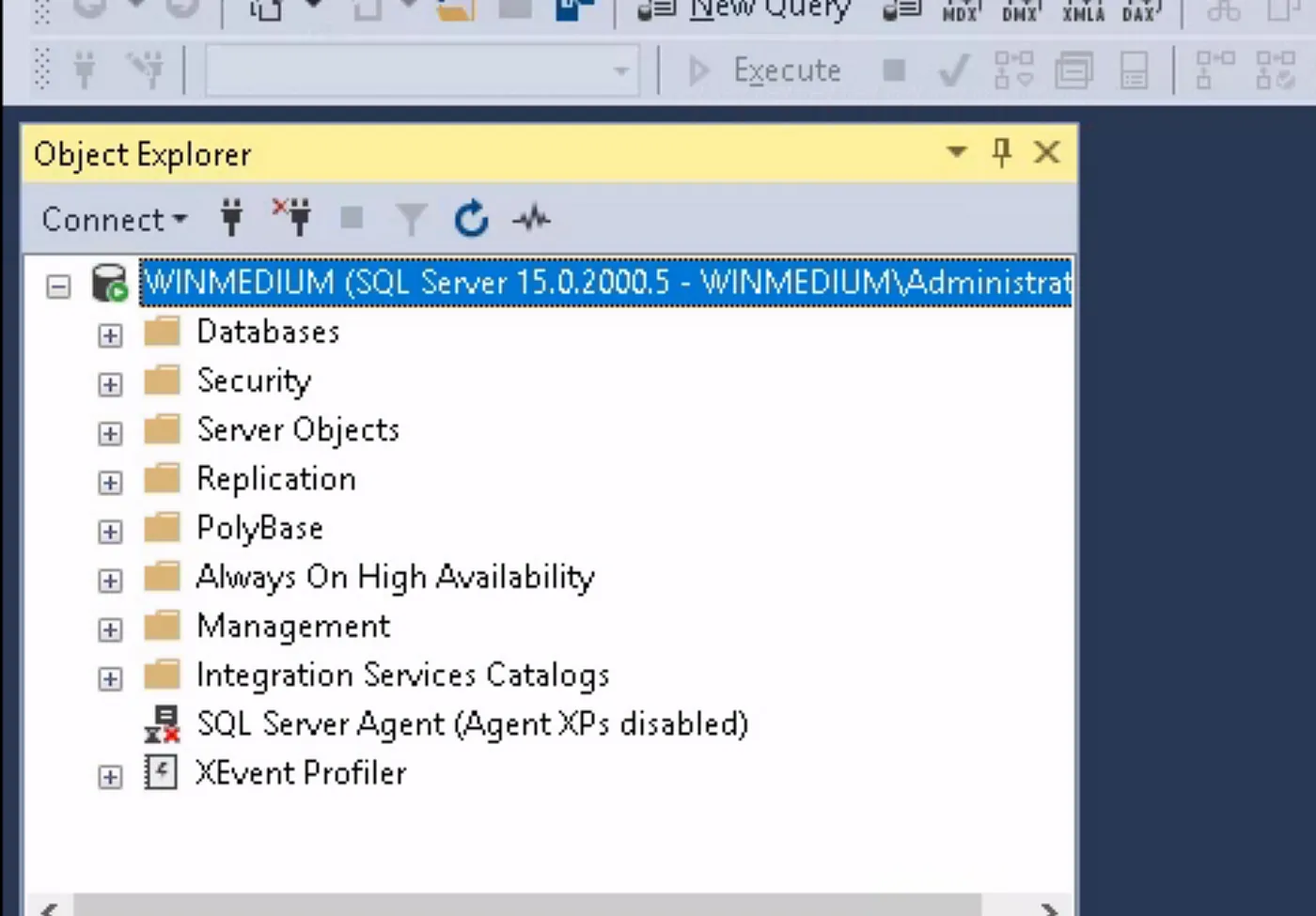
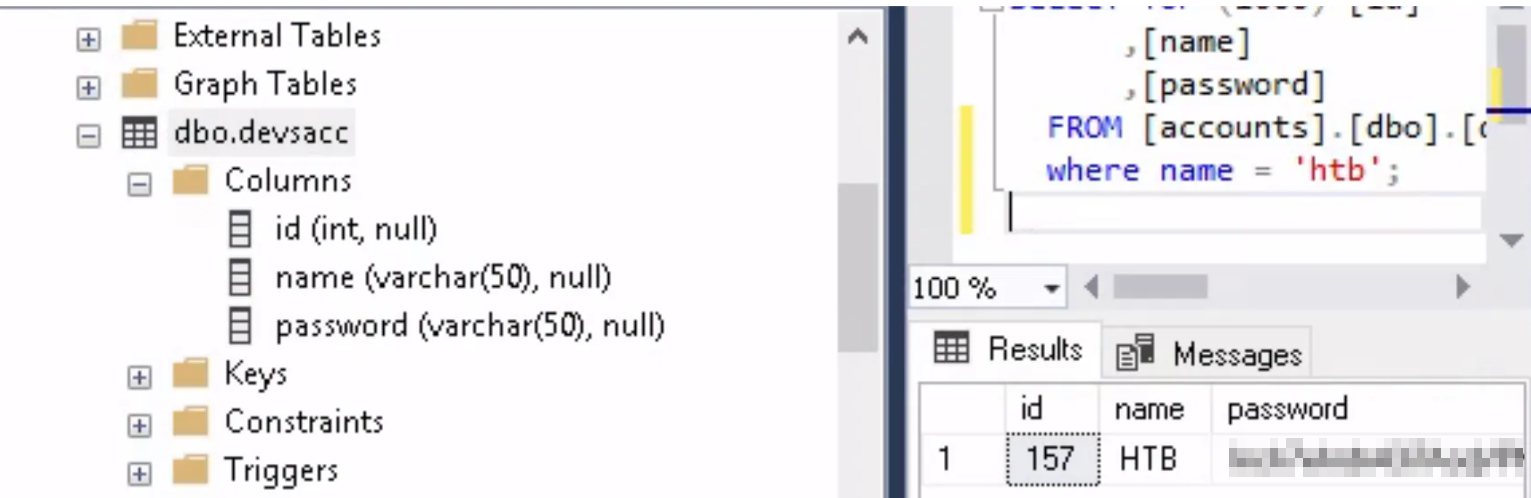
And we successfully connect! Now, we can search the structure for interesting objects. Since we are looking for the password of the user “htb,” we should definitely check the `dbo.devsacc` table.
With a simple query, we can extract the password of the “htb” user.