While infilatrating a system it is mostly necessary no escalate your privileges to another user or the root user. While learning about priv-esc on linux-system I often used a simple technique which is based on misconfigured binarys. For example if a lower priv user is allowed to run a program with sudo and no password promp you can use this to get a root shell.
I found on trainings vm’s that it was possible to run vi/vim with sudo privileges and no needed password. You can find a list about other binarys that can be used here. In my last post we used tar to escalate our privileges to root.
So let’s start first of all we check our user privileges:
sudo -l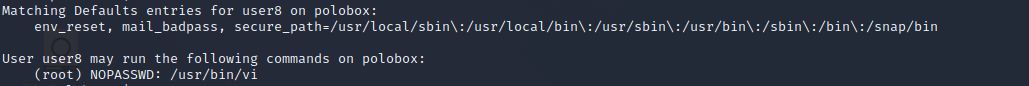
As we can see vi can be run as root with no password authentication. Now we start vi with superuser privileges and enter the command-mode.
As final step we enter:
:!shto spawn our root shell. And that’s it, now we are root.

Das klappt nicht
…weil?
Also es klappt bei dir nicht oder klappt es grundsätzlich nicht?
Steht dir gerne frei, es in der entsprechenden Umgebung bei zB THM zu testen:
TryHackMe – Common Linux Privesc
Grüße,